6 min to read
CountZero R1 challenges
Task [write-up]

Challenges list
- Packets Primer
- Shark on wire 1
- Wireshark doo dooo do doo
- Easy101
- Filteration-01
- Wireshark twoo twooo two twoo
- ARP Storm
Note: These challenges from (PicoCTF, JISCTF, CyberTalents)
Challenge [1] | Packets Primer
- Hint: Follow the stream
- Flag format: picoCTF{some words here}
According to the hint, just follow the tcp stream & you will get the flag:


To remove the space between each character & get the right flag, we can use Cyberchef like that:

Flag: picoCTF{p4ck37_5h4rk_b9d53765}
Challenge [2] | Shark on wire 1
- Hint: Follow follow follow follow
- Flag format: picoCTF{some words here}
Again, hint is saying follow !! so we have a udp stream here.. lets follow it:


Nothing useful in the first stream, so let’s check next streams:

I found the right flag after 5 streams ( in stream n. 6 )
Flag: picoCTF{StaT31355_636f6e6e}
Challenge [3] | Wireshark doo dooo do doo
- Hint: They said that ROT13 cipher is simple & the Chef know it
- Flag format: picoCTF{some words here}
First thing, we don’t have a clear point to start… So I decided to check the exists protocols first:
Statistics > Protocol Hierarchy:

I noticed that TCP have 99.8% of packets:

So let’s go to analyze TCP packets
Just add tcp filter to show only TCP packets, go to packet number 1 and follow tcp streams like that:

The first stream has no interesting data… it is just POST HTTP Request with some encrypted data about Kerberos (network protocol) :

Going through next streams we will get a rot13 data seems to be the flag in stream number 5 :

After decrypting it using Cyberchef You will get the flag:

Flag: picoCTF{p33kab00_1_s33_u_deadbeef}
Challenge [4] | Easy 101
- Hint: It is the same challenge that we solved in fitst task in session 3, but the flag need a Chef ! (Our Chef rotated the flag with 13 & then encoded it by Base64)
- Flag format: JISCTF{some words here}
From the hint, I remember that we could solve this challenge by many ways such as (follow stream) or (export objects) … etc. So, when exporting the http objects, I noticed that there is a file name encoded in base64 !!


Just 1 click on these data will bring us to the packet that contains the base 64 values:

You can get the value by (show packet bytes) like that:


After using cyberchef on it I got this rot13, so by decrypting it from Rot13 again I got the flag:


Flag: JISCTF{JUST_S1MPL3_PC4P_F1L3_4N4LYS1S}
Challenge [5] | Filteration-01
- Hint: ICMP packets maybe useful, use a filter to display them
- Flag format: JISCTF{some words here}
From the hint, adding icmp filter to show icmp traffic only:

As we know the flag format starts with JISCTF, If we click on the first packet (Ping Request), We can notice that there is a J character in the packet bytes area
The second one which is (Ping reply) has a different syntax which contains @ instead:

The 3rd one has the same syntax of the first packet but with I character… So, there is a 1 character of flag in every (Ping request) packet!
You can filter out (ping response) to decrease the number of the displayed packets and then follow packets 1 by 1 to get every character of the flag, (OR) without filtering, you can get it also!
icmp.type eq 8 or icmp.type == 8 filters will show only ping request packets
The final flag with all characters will be:
Flag: JISCTF{M4LW4R3_3XF1LT3R4T10N_US1NG_1CMP_TTL}
Challenge [6] | Wireshark twoo twooo two twoo
- Hint: Attackers can use Amazon servers maliciously, don’t waste your time on Google DNS it is official
- Flag format: picoCTF{some words here}
From the hint, I’m dealing with DNS packets so first thing I added dns filter, then I filterd out Google DNS because it is official (as hint said!!) using
!(ip.addr == 8.8.8.8) filter
So, our filter will be like that: dns && !(ip.addr == 8.8.8.8)
After adding the 2 filters we will get only 42 displayed packets from 4831.. Amazing !!

As we see there are too many domains, but if you back to the hint you will see “Attackers can use Amazon servers” !! so we can just add one more filter to show only packets that contains “amazon” with this syntax: && frame contains "amazon"
Note: The final filter will be dns && !(ip.addr == 8.8.8.8) && frame contains "amazon"
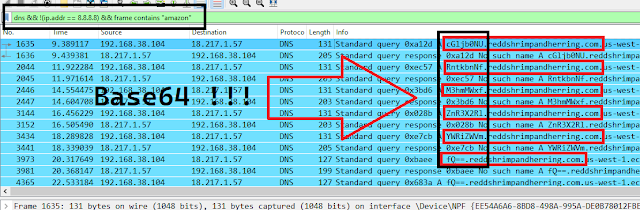
As we can see in the last image there are base64 data placed as subdomains, ignore the other packets which are “query response” and extract these values:
cGljb0NURntkbnNfM3hmMWxfZnR3X2RlYWRiZWVmfQ==
Just decode it from base64 and you will get the flag !
Flag: picoCTF{dns_3xf1l_ftw_deadbeef}
Challenge [7] | ARP Storm
- Hint: An attacker in the network is trying to poison the arp table
- Flag format: flag{some words here}
The given pcap file only contains ARP traffic, no (follow stream) or (export objects), there is just some information in info column that say Uknown ARP opcode 0xvalue...
If u noticed the packet bytes you will see this opcode in ASCII format which is “Z” for the first packet and “=” for the last packet, so it seems to be Base64 !!


You can extract these values by each packet … and then decode it with Cyberchef to get the flag.
Flag: flag{gr@tuit0us_0pcOde_1s_Alw@ys_A6uSed_t0_p01s0n}
Note: You can extract data from ARP Storm & Filteration-01 by using Tshark tool easly.



