11 min to read
CTI 101 Notes
CyberThreatIntelligence101 Notes

This is my notes for CTI101 Course. You can find the course Here
Table of Contents
- Objectives of Threat Intelligence
- Introduction to Threat Actors
- Threat Vectors
- The Intelligence Cycle
- Introduction to Law and Ethics
- Resources
Objectives of Threat Intelligence
Cyber threat intelligence (CTI)
CTI is the gathering of information from various sources about current or potential threats to an organization.
“CYBER”
The word ‘cyber’ denotes a relationship with information technology (IT), i.e., computers. (It can relate to all aspects of computing, including storing data, protecting data, accessing data, processing data, transmitting data, and linking data.)
“THREAT”
- A ‘threat’ is a statement indicating the will to cause harm to or create some other kind of negative consequences for someone.
- Many threats involve a promise to physically harm someone in retaliation for what they have done or might do. Some threats are simply meant to intimidate, and don’t involve pressuring someone to do something. Not all threats involve violence.
- A security threat is someone or something that might make a situation unsafe.
- Threat can also mean a warning or sign that harm or trouble is coming.
“INTELLIGENCE”
- ‘Intelligence’ describes the practice of collecting, standardizing and analyzing data that is generated by networks, applications, and other IT infrastructure in real-time, and the use of that information to assess and improve an organization’s security posture.
- “Intelligence is knowledge and foreknowledge of the world around us – the prelude to decision and action…” - US Central Intelligence Agency (CIA)
- “Intelligence is information that is received or collected to answer specific questions on who, what, where, when, how and why…” - UK National Crime Agency (NCA)
Notes:
- CTI feeds from and into all of other cyber security fields such as:
- Security Operation Center (SOC)
- Incident Response (IR)
- Patch & Vulnerability Management
- Human Resources …
- CTI creates deeper insight into the nature of the threat and how it can be countered
- CTI helps cyber security to move from reactive to proactive
Indicators of compromise (IOCs)
Are pieces of forensic data, such as data found in system log entries or files, that identify potentially malicious activity on a system or network.
CTI in practice within an organization:
- SOC → feeds into tangible security such as firewalls IOC.
- IR → attributes an attack to a defined group or individual.
- Path & Vulnerability Management → prioritization.
- Human Resources → policy around areas like crisis management.
- Business Risk Management → cyber has impact on all business areas.
Basic Web Layers:
- Surface Web
- Deep Web
- Dark Web
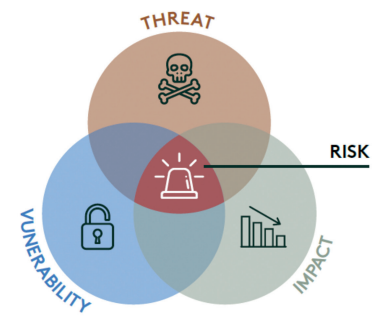
Risks risk is defined as a combination of threat, vulnerability and impact.
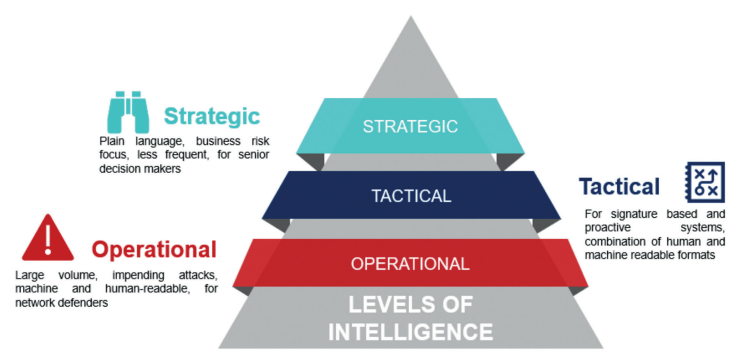
Levels of Intelligence from an organizational perspective:
- Strategic Level -> The ‘board’ and senior decision makers.
- Operational Level -> SOC operations and security controls applications.
- Tactical Level -> Threat Hunting within log files
Actionability: Threat Intelligence that a decision maker can take action on.
Note: The usefulness of cyber threat intelligence is predominantly based on its ‘actionability’ from an organizational standpoint.
Different sources of intelligence:
- Indicators of compromise (IOCs)
- Client-derived data
- Deep & Dark web
- Messaging platforms
- Social media
- Human intelligence
- Malware analysis
- Geopolitical developments
- Code repositories
- Paste sites
- Information sharing platforms
Why organizations need/use CTI ?
- Identify and assess potential threats to their networks and systems.
- Enhance their overall security posture by proactively taking measures to prevent attacks.
- Improve incident response efforts by having up-to-date information about known threats.
- Priorities resources for the mitigation of high-risk vulnerabilities.
- Monitor external sources for signs of a potential breach or attack.
- Stay informed about the tactics, techniques, and procedures used by malicious actors.
CTI Analyst:
A Cyber Threat Intelligence Analyst is a specialized role within an organization and the wider professional practice of cyber security.
The roles and responsibilities of a CTI Analyst includes:
- Identifying organizational intelligence requirements
- Collecting relevant data and conducting all-source analysis to inform decision making process
- Identifying, monitoring, and assessing potential threats or weaknesses
- Validating that security qualifications and requirements are met
- Creating reports that highlight key findings for security teams and other members of the organization
- Presenting findings to other teams and proposing counteractions to mitigate threats
Introduction to Threat Actors
Hackers:
- A ‘hacker’ is an individual who uses computer, networking or other skills to overcome a technical problem.
- The word has been used over the years to refer to anyone who uses their abilities to gain unauthorized access to systems or networks in order to commit crimes.
- A hacker may, for example, steal information to hurt people via identity theft or bring down a system and, often, hold it hostage in order to collect a ransom.
Types of Hackers:
- Black Hat: conducts hacking activities without owner consent and with malicious intent.
- White Hat: conducts hacking activities with consent of the technology owner.
- Gray Hat: conducts hacking activities without owner consent but usually stops short of malicious activities.
Black Hat Hackers Types:
- NATION STATE ACTORS:
- Nation State Actors work for governments to disrupt or compromise other target governments, organizations or individuals to gain access to intelligence or valuable data.
- They have been known to create significant international incidents.
- Generally speaking they can operate without fear of legal retribution in their home country and are often part of ‘hackers for hire’ companies aligned to the aims of a government or dictatorship.
- CYBER CRIMINALS:
- Cyber Criminals are individuals or teams of people who commit malicious activities on networks and digital systems, with the intention of stealing sensitive organization data or personal data, and generating profit.
- It’s important to note that the distinction between cyber criminals and nation state actors is becoming increasingly blurred.
- They are normally always motivated by financial gain.
- HACKTIVISTS:
- Hacktivists generally operate within the social or political sphere, breaking into and causing damage to computer systems and networks.
- Targets of hacktivists can vary dramatically from things like the Church of Scientology, to pharmaceutical companies and drug dealers.
- Hacktivism is a combination of the words ‘Hacking’ and ‘Activism’.
- One of the most (in)famous hacktivist groups of recent times would have to be Anonymous, and they are well worth doing some reading on.
The 3 primary ways of measuring threat actors:
- Motivation: Why an Actor is doing what they are doing.
- Capability: What is Actor’s ability to achieve their Intent.
- Intent: What an Actor is hoping to achieve.
CIA Triad:
‘CIA triad’ stands for Confidentiality, Integrity, and Availability. It is a common model that forms the basis for the development of secure systems.
- Confidentiality: Confidentiality is to do with keeping an organization’s data private. This often means that only authorized users and processes should be able to access or modify data.
- Integrity: Integrity means that the data can be trusted. It means that it should be maintained in a correct state, kept so that it cannot be messed around with, it should be correct and also needs to be reliable.
- Availability: It’s all well and good maintaining confidentiality and integrity but the data must be available to use. This means keeping systems, networks and devices up and running.
Mandiant’s APT1 Report highlights:
- Advanced persistent threats (APTs) are real and pose a significant threat to organizations.
- APT actors are highly organized, well-funded and operate with a long-term perspective.
- APT actors often target specific organizations and industries for extended periods of time.
- APT actors typically exfiltrate data slowly over time, often using encrypted channels to evade detection.
- APT actors may reuse tools, infrastructure, and tactics across multiple attacks, providing opportunities for attribution and tracking.
- APT actors often seek to maintain a persistent presence within an organization’s network to support ongoing operations.
- APT actors can evade detection for long periods of time by using stealthy techniques and customizing their tactics for each target.
- APT actors use a combination of technical and social engineering tactics to compromise organizations.
- Detecting and responding to APT actors requires a multi-faceted approach that includes regular monitoring and auditing of networks, systems, and user activity.
Threat Vectors
Threat Vector is a path or method via which threat gains access to a victim computer or network.
Note: Threats can exploit vulnerabilities in Emails, Users, Software, Networks, Host, Remote Access Portals.
Security Controls:
countermeasures that a company can implement to detect, prevent, reduce or counteract security risk(s). such as:
- Isolating legacy systems
- Education and training
- Physical Security (i.e. no USB)
Attack Surface
- The combined sum of the different points within an organization that a malicious cyber actor can use to mount an attack.
- This includes everything from the visible interfaces like websites or apps, to the underlying protocols and technologies that enable communication and data exchange.
- The goal of understanding the attack surface is to identify the potential weaknesses in a system and prioritize the most pressing threats. This information is then used to inform and guide the development of mitigation strategies that can help prevent successful attacks and keep the target system and its data secure.
Watering hole attack
- Attackers find a suitable website (The Watering Hole)
- Attackers compromise the website
- User visits the website and malicious script is downloaded
- Script exploits vulnerabilities and delivers malware to the user
- Attackers have access to the network and continue trying to reach their objective
Notes:
- Cyber Criminals have pivoted toward VPN and RDP logins because logging into victim network requires no malware, which means much smaller trace for defenders to detect.
- Supply chain vulnerabilities have the ability to sit behind all of the threat vectors that we have discussed.
- Common Vulnerabilities and Exposures (CVE) is a standardized method for recording vulnerabilities.
- TTP stands for Tactics, Techniques, and Procedures.
- APT stands for Advanced Persistent Threat.
The Intelligence Cycle
The process of developing raw information into finished intelligence for an end consumer..
- Direction: where the intelligence team takes direction from the customer (intelligence requirements).
- Collection: where the intelligence team collects data and turns into information.
- Analysis: where information is turned into intelligence.
- Dissemination: where the intelligence is handed back to the client, which in turn stimulates new Direction…
Data vs Information vs Intelligence
- Data refers to simple facts that tend to be available in large volumes. In the context of cyber security, IP addresses or logs are typical examples. By itself, raw data is of limited utility.
- Information is produced when this data is collated to provide a useful output – for example, a collated series of logs showing a spike in suspicious activity.
- Intelligence comes from the processing and analysis of this information and can be used to inform decision making. For example, the collated log data is contextualized with prior incident reports regarding similar activity, which also allows for the development of a strategy to mitigate the incident.
The intelligence cycle and its steps can be communicated in different ways dependent on who you speak with but some of the key elements that everyone can agree with sit below:
- Defining what information is needed to support decision-making and security operations.
- Gathering data from various sources, such as open source intelligence (OSINT), proprietary databases, and sensor networks.
- Converting raw data into usable information by verifying, validating, and fusing it into a coherent picture.
- Assessing the significance of the information and identifying patterns, trends, and potential threats.
- Sharing the results of the analysis with stakeholders who need it to make informed decisions and take appropriate actions.
- Using the results of the analysis to inform future collection and analysis efforts, as well as to validate the accuracy and reliability of the information.
By following this structured process, organizations can ensure that they have a complete and up-to-date understanding of the cyber threat landscape, and can take effective steps to protect themselves from potential threats.
Introduction to Law and Ethics
Laws are structured rules that are used to govern society.
Ethics are generally considered as moral values that an individual may establish as their own personal rules to live by.
Note: You can be fired for not following company ethical guidelines even though you haven’t broken any laws.
Difference between Law & Ethics:
| Factor | Law | Ethics |
|---|---|---|
| At its core | Set of rules and regulations not to break | Set of guidelines that a person should follow |
| Governed by | Government and enforced by the judiciary and police | Individual, Legal and Professional norms |
| Penalty for infringement | Custody or fine | Sanction |



