6 min to read
Malware Traffic Analysis 2
CTF challenge [write-up]

Challenge Requirements:
- Wireshark
- Network Miner
- BrimSecurity & Suricata (Just follow the video instructions on the details page)
- VirusTotal Website
- PE Tool (Such as PeStudio, Winchecksec or psec in Linux)
Follow the challenge details & instructions from here before the start.
You can find the challenge questions here
given a .zip file: c05-MalwareTrafficAnalysis2.zip which contains a pcap file (The password of zip is: cyberdefenders.org)
Lets analyse the file and answer the questions…
Q1. What is the IP address of the Windows VM that gets infected?
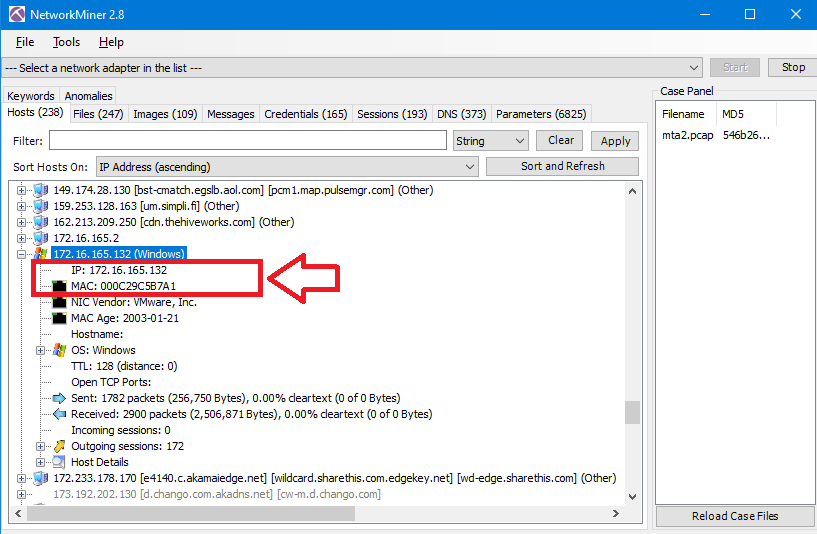
By using NetworkMiner, we can get the IP & MAC addresses of the infected Windows VM:
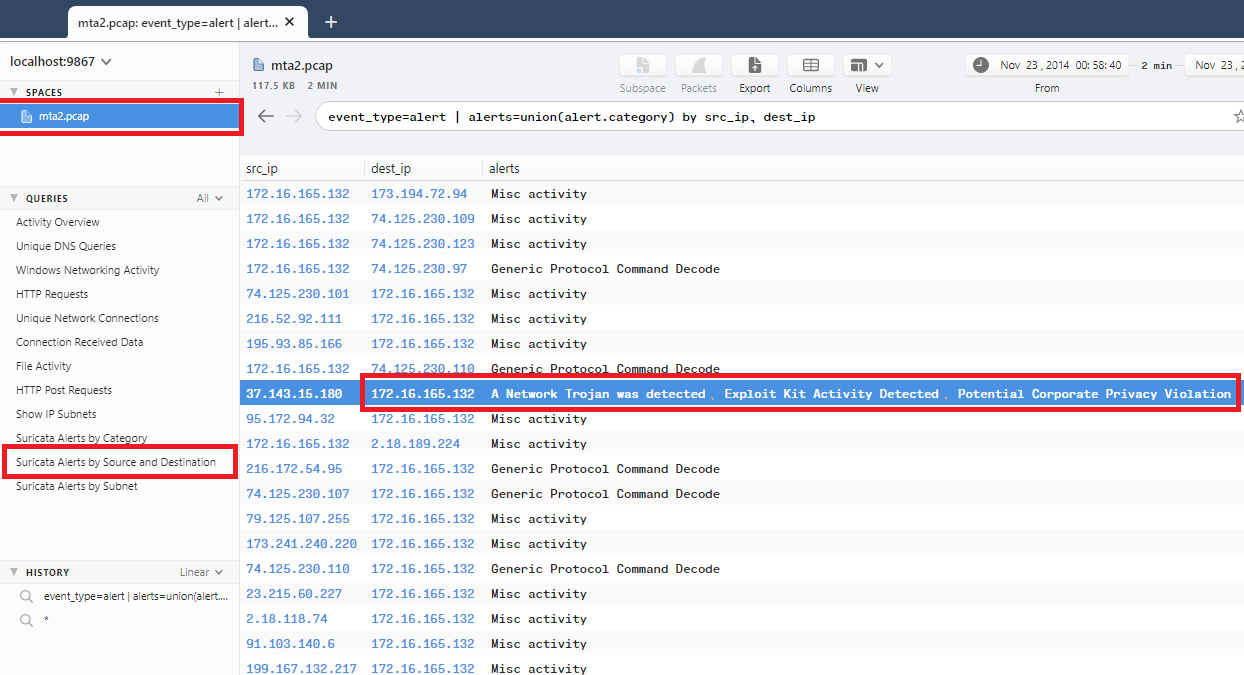
We can use Brim to make sure that the IP address is 172.16.165.132:
Q2. What is the MAC address of the infected VM?
Already solved in the previous question.
Q3. What are the IP address and port number that delivered the exploit kit and malware?
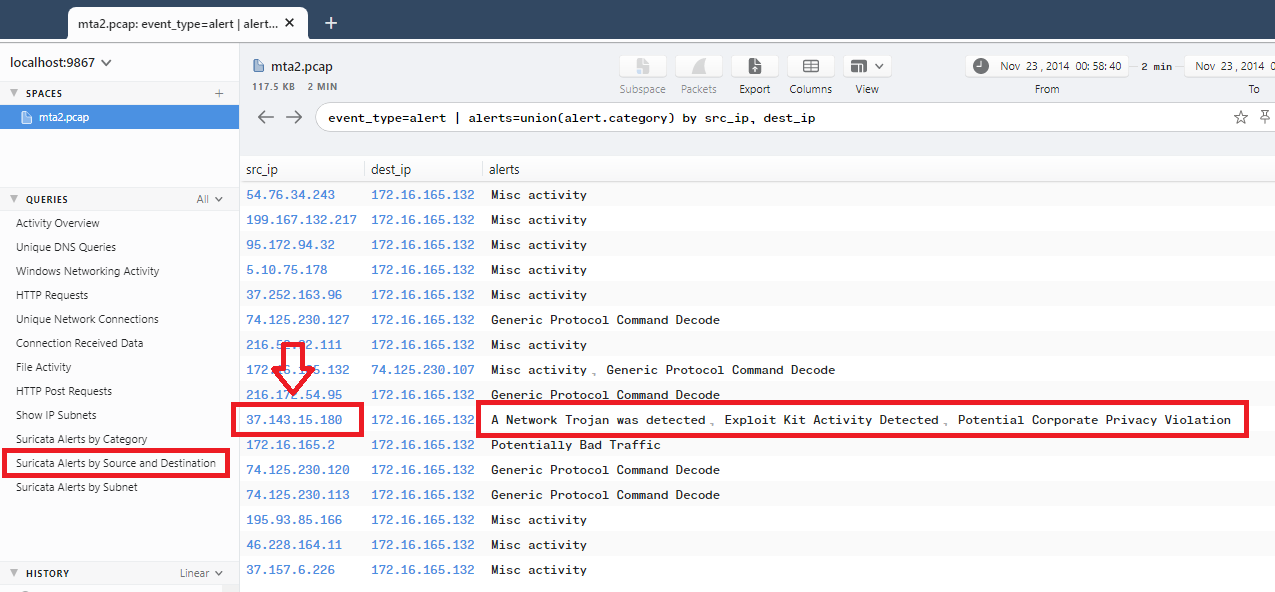
Checking suricata logs in Brim again, the IP is 37.143.15.180:
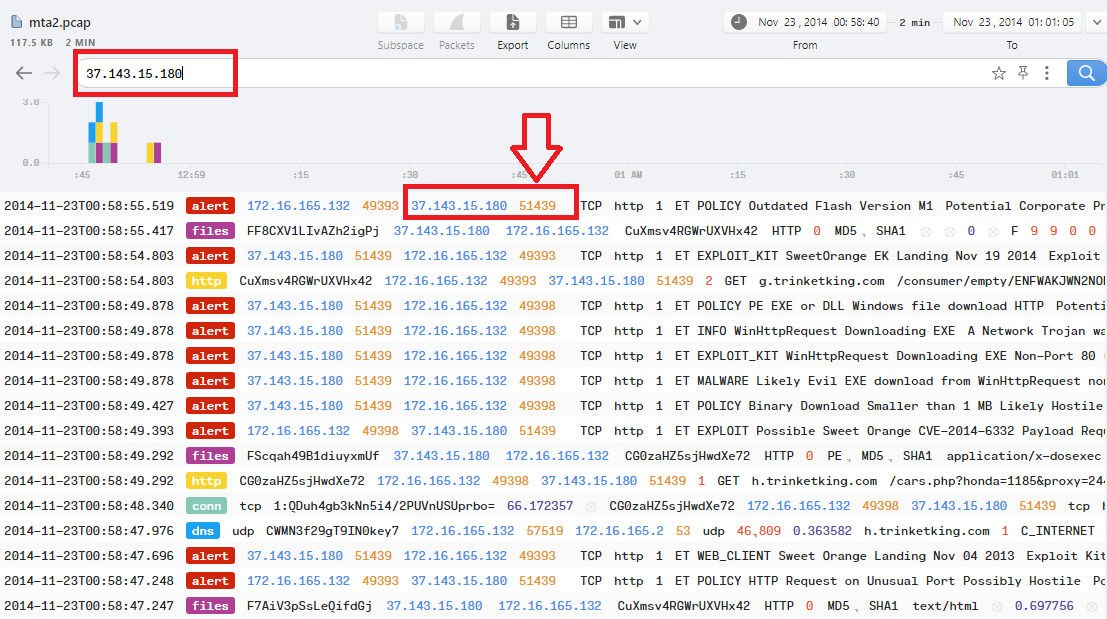
To get the port number associated with this IP, just filter the logs with the IP and you will get the port which is 51439:
You can get it from Hosts tab in NetworkMiner also:
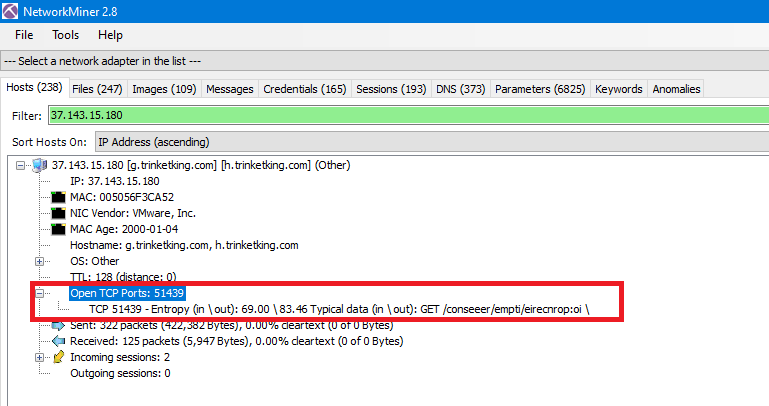
Q4. What are the two FQDN’s that delivered the exploit kit? comma-separated in alphabetical order.
Just filter the data in Brim with 37.143.15.180 | sort ts to show only connections and alerts related to the IP that delivered the Exploit Kit:
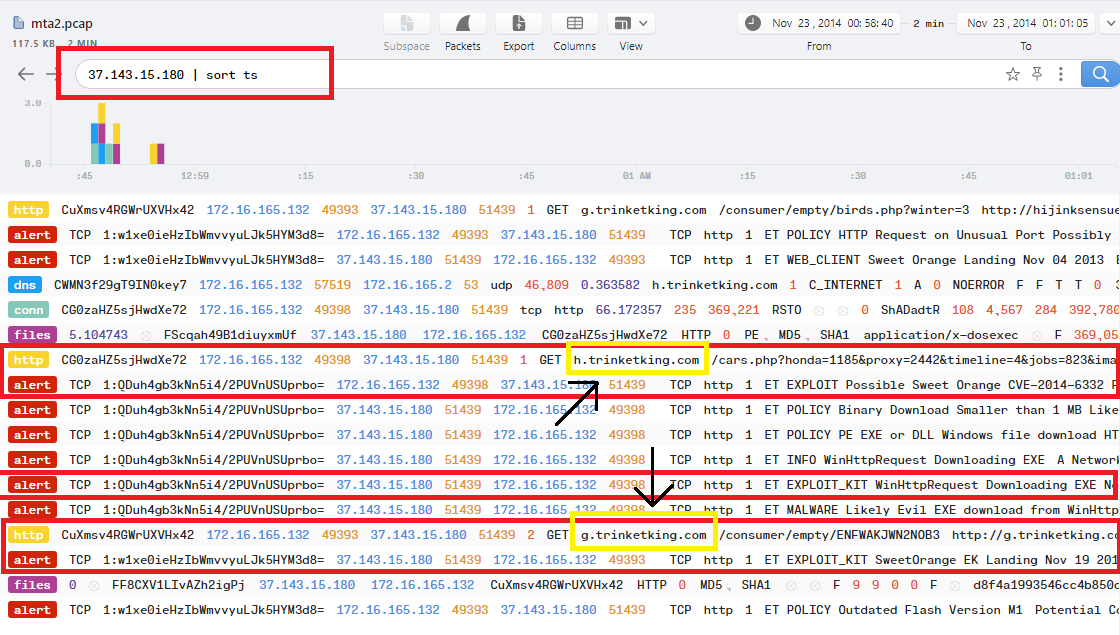
As you can see in the image, an http connection to h.trinketking.com happened before the first alert of the Exploit Kit, and another http connection to g.trinketking.com happened before the second alert of the other Exploit Kit.
So, The answer will be g.trinketking.com,h.trinketking.com
You can also get the answer from last image in the previous question.
Q5. What is the IP address of the compromised web site?
By Checking HTTP Conversations from statistics in Wireshark.. The conversation from the infected host 172.16.165.132 to this IP 192.30.138.146 has the most number of packets (1376):
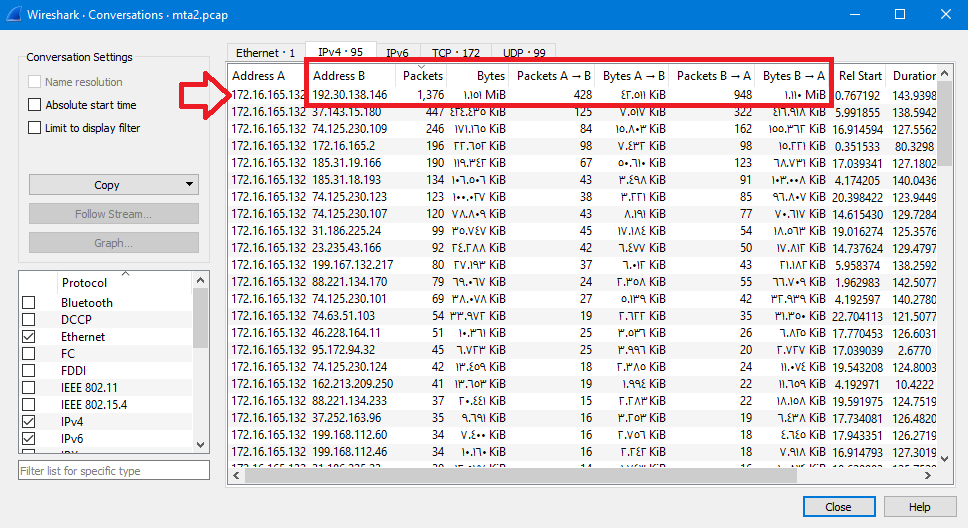
Checking HTTP Endpoints show the same result that IP 192.30.138.146 has the most number of packets (1376) after the infected host (4682):
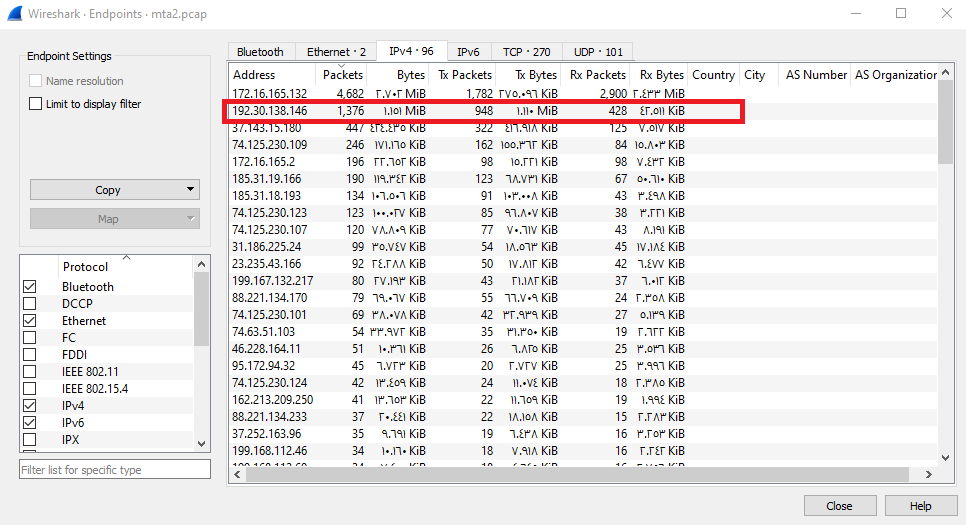
tried to submit this IP and it was the correct answer.
Note: To solve this type of questions, just follow the referrers starting from the website that devlivered the exploit-kit to the first website which the victim opended such as google.com or bing.com … etc. and you will find the compromised website which redirects the victim to all other pages including the page that delivered the EK.
Q6. What is the FQDN of the compromised website?
In Wireshark, if We use this filter ip.addr == 192.30.138.146 && http to show the HTTP connections related to this ip, We will get the hostname or FQDN of it:
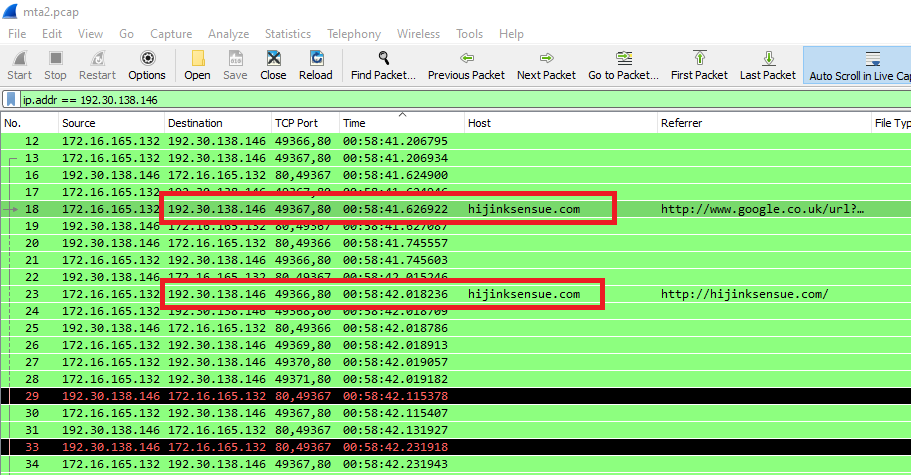
Same result in Brim:
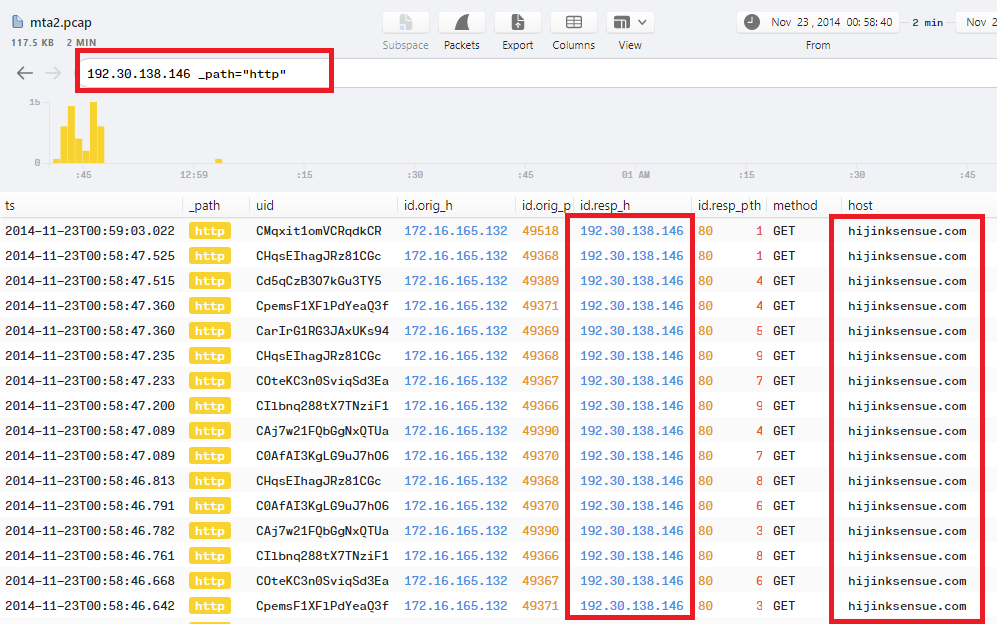
So the answer will be hijinksensue.com
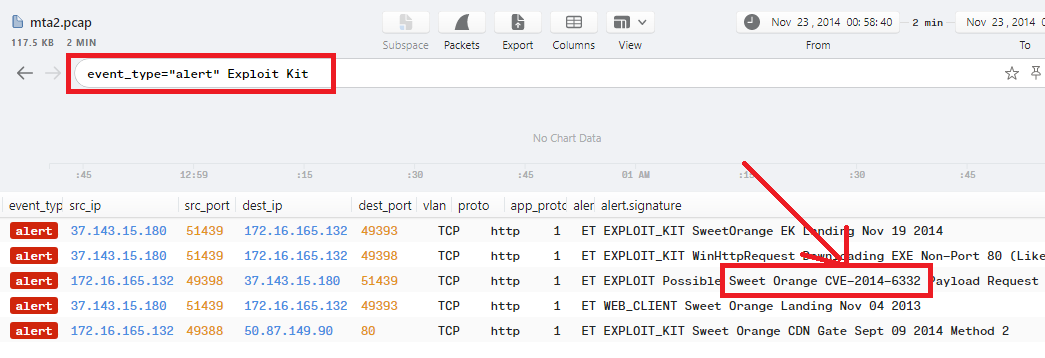
Q7. What is the name exploit kit (EK) that delivered the malware? (two words)
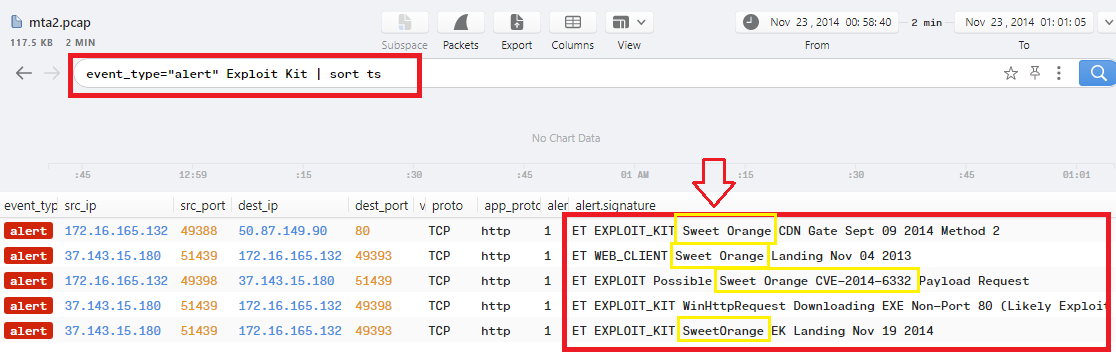
In Brim, just use event_type="alert" Exploit Kit to show alerts that contains “Exploit Kit” to get the name of the Exploit Kit which is Sweet Orange:
Q8. What is the redirect URL that points to the exploit kit landing page?
To find the landing page of the exploit kit, I checked all http connections related to the exploit kit alert logs in the previous image in question7 and I found something interesting..
just double-click on the last alert which contains ET EXPLOIT_KIT Sweet Orange CDN Gate to show its details, click on conn to show the connections, and then select http to check the http connection as the following images:
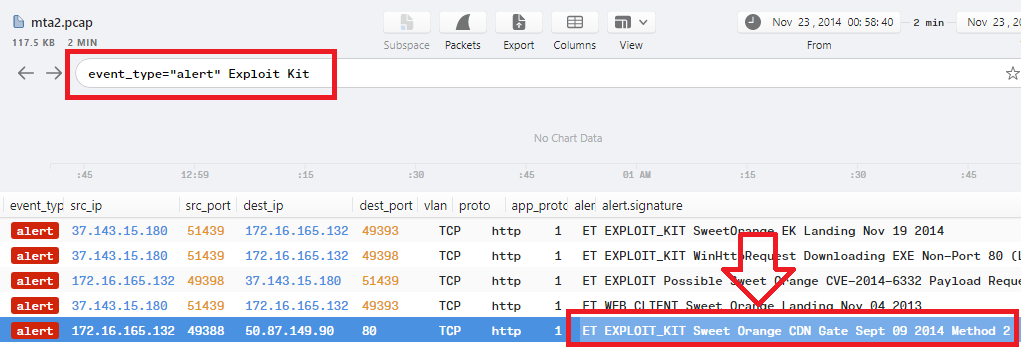
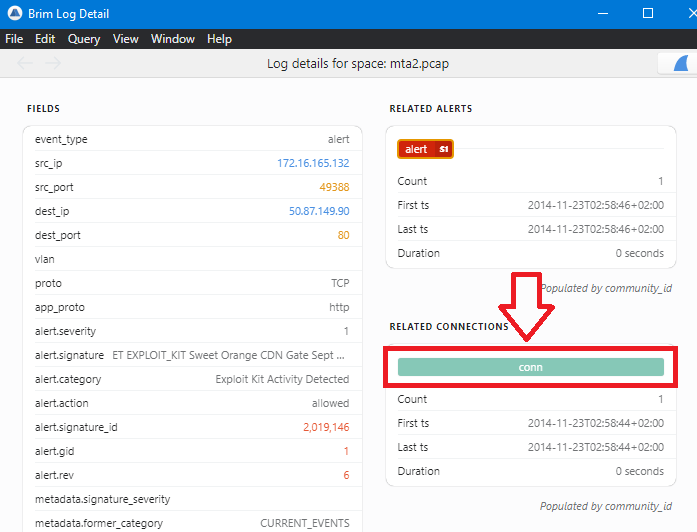
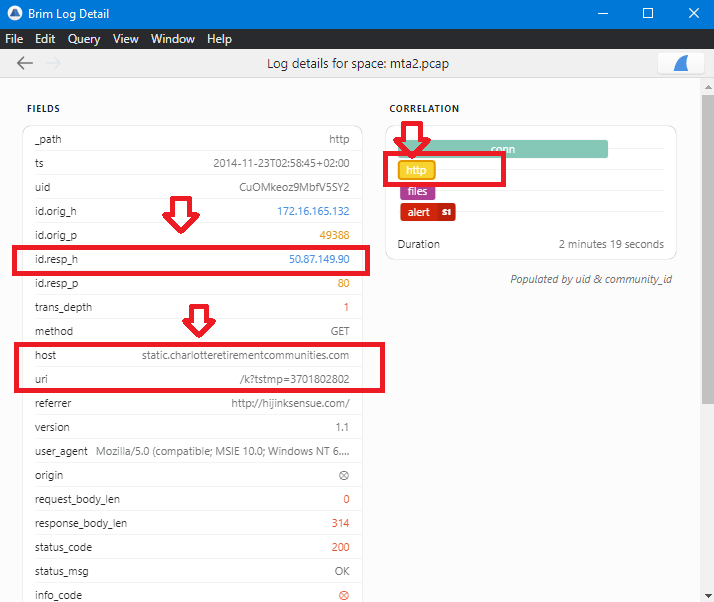
In the previous image, there is an http request before the alert which sending a GET request to host: static.charlotteretirementcommunities.com with uri: /k?tstmp=3701802802 and its IP is 50.87.149.90 …
since the answer format matches the url format that we found, the answer will be the full url (host+uri) which is static.charlotteretirementcommunities.com/k?tstmp=3701802802.
Q9. What is the IP address of the redirect URL that points to the exploit kit landing page?
I got the IP in the previous question.
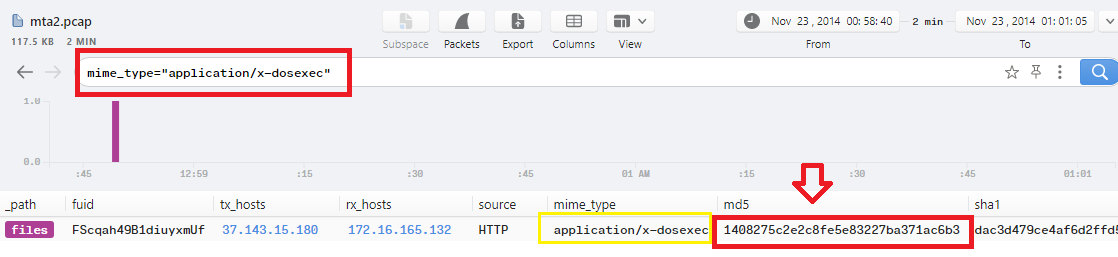
Q10. Extract the malware payload (PE file) from the PCAP. What is the MD5 hash?
I used this filter mime_type="application/x-dosexec" to show the executable files in Brim logs and I have found only 1 file with md5 hash: 1408275c2e2c8fe5e83227ba371ac6b3 and this is the correct answer:
If you are using Wireshark, just go to Export Objects > HTTP and search for application files that related to the the host which delivered the exploit-kit (we got it in question4 already)..
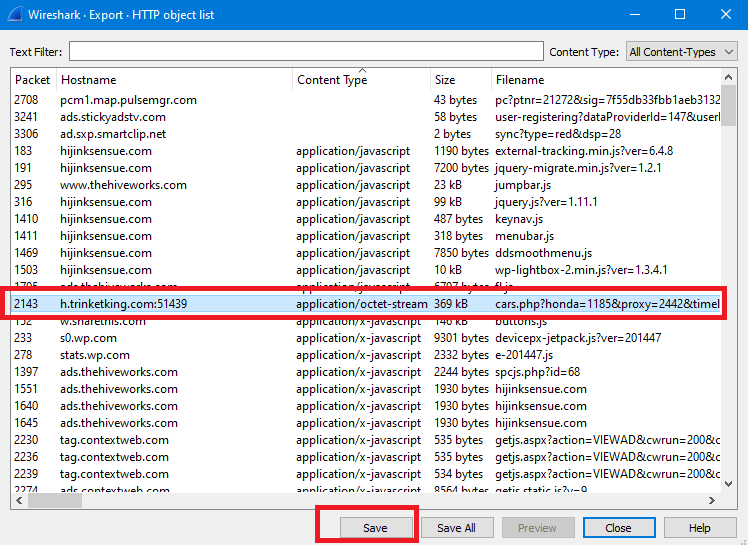
Save it and then upload the file on VirusTotal to get the MD5 hash.
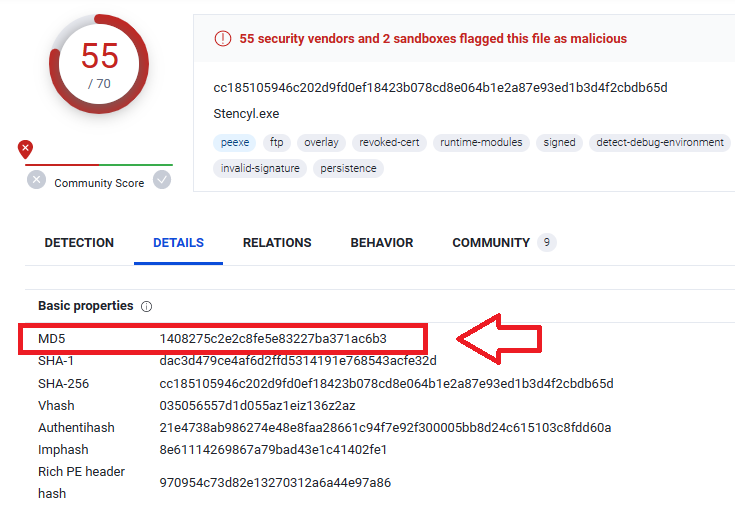
Q11. What is the CVE of the exploited vulnerability?
According to Question7, using the same filter event_type="alert" Exploit Kit in Brim will show the CVE which is CVE-2014-6332 as we can see:
Q12. What is the mime-type of the file that took the longest time (duration) to be analyzed using Zeek?
In Brim, We can filter logs to show only files and sort them with the (duration) using this filter _path="files" | sort -r duration:
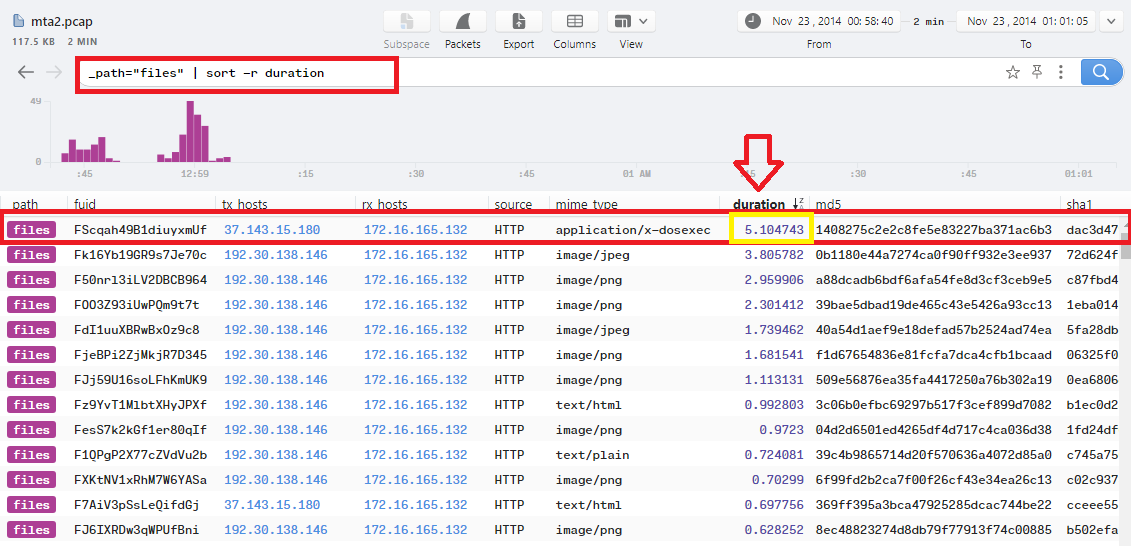
As we can see, the mime-type is application/x-dosexec which is the PE file that we got before.
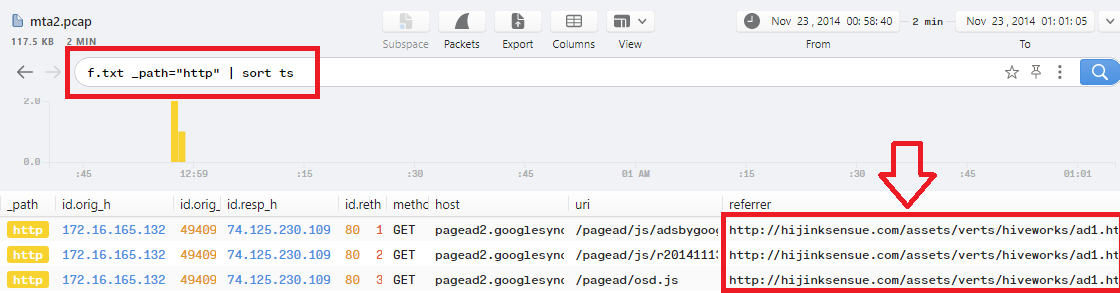
Q13. What was the referrer for the visited URI that returned the file “f.txt”?
In Brim, add this filter f.txt _path="http" | sort ts and scroll right to see the referrer which is http://hijinksensue.com/assets/verts/hiveworks/ad1.html:
Q14. When was this PCAP captured?
You can get it easly in Brim as the following image:
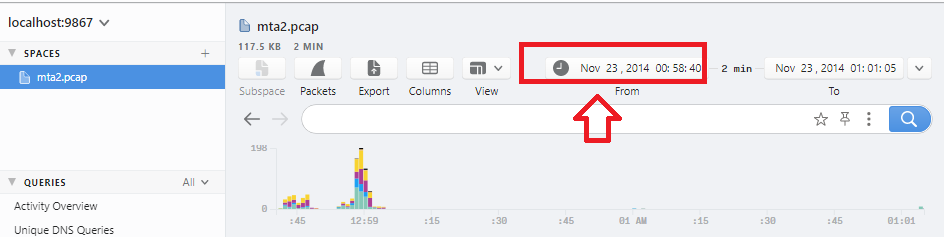
The answer will be 23/11/2014.
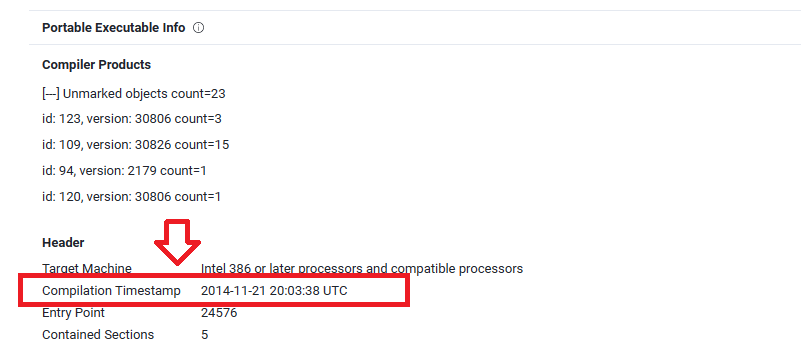
Q15. When was the PE file compiled?
Back to Question10, check details page on VirusTotal, scroll down and check Portable Executable Info and you will see that Compilation Timestamp is 21/11/2014:
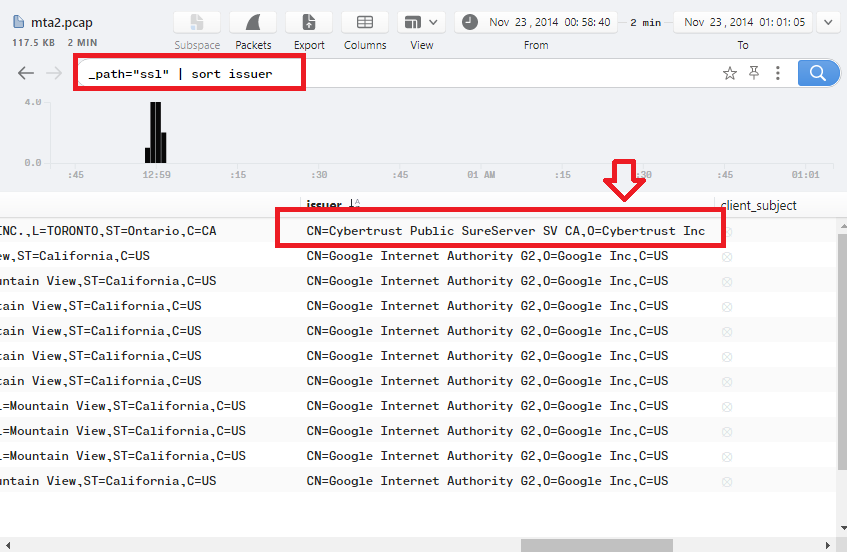
Q16. What is the name of the SSL certificate issuer that appeared only once? (one word)
In Brim, use _path="ssl" | sort issuer filter and go to the issuer column, you will find that Cybertrust appeared only once:
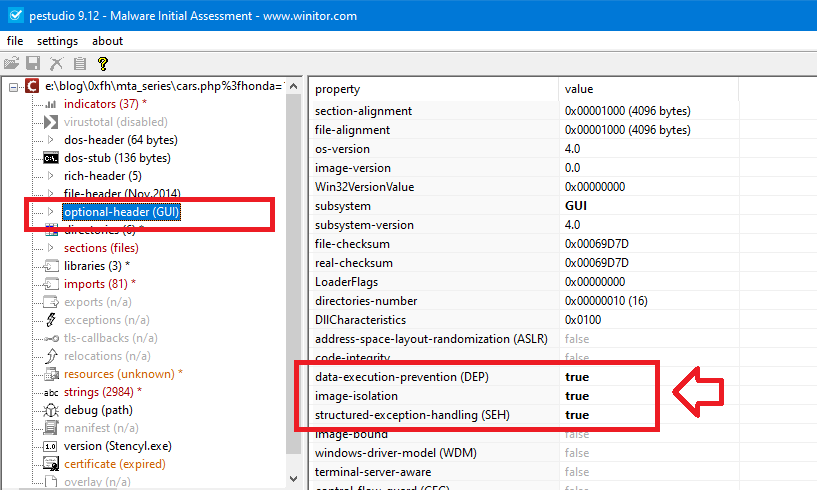
Q17. What were the two protection methods enabled during the compilation of the present PE file? Format: comma-separated in alphabetical order
To check the protection methods of the PE files, We have many tools such as PeStudio, Winchecksec, pesec … etc.
- Pestudio output:
- pesec output:
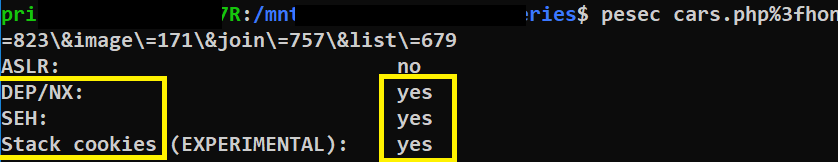
Since the answer format needs only 2 methods and starts with ‘D..,…’ , then the right answer will be DEP,SEH.



